Most of us travel for longer holidays or business trips, at least a few times a year. It is likely that during such a trip or a small break between travelling, many will decide to grab a moment and write one last email or finish some task.
For this reason, in this article, we will focus on the dangers that can lurk on us in public spaces, precisely when we travel, either on trains or while in a cafe.
You’ve certainly used public Wi-Fi at least once in your life.
Perhaps you had to check the train schedule, or maybe you wanted to scroll through your favourite social media.
However, has it occurred to you, to consider what are the consequences of using an open Wi-Fi network (by open Wi-Fi, I mean one that doesn’t need any password to connect and one to which the password is available to everyone).
The problem is that we don’t really know, at first, who is connected to such a network, and second, we don’t know if the PKP_Free_Wifi network is a network set up by PKP.
Using such a network can be compared to letting a cybercriminal into our home network, yet we wouldn’t want a stranger to be able to overhear what we do online. Of course, we can’t immediately say that every public network is created by, e.g. a hacker, however, I personally think that this approach is better than connecting to open networks. Having said that, to give a better idea of the potential dangers of using public Wi-Fi networks, I’ve outlined two major attacks below:
This attack commonly consists of cybercriminals creating their hotspot or using the Evil Twin attack. Cybercriminals will create fake Wi-Fi networks that look like the real ones (such as a hotel network) but are controlled entirely by an attacker.
The whole thing can also be done on real Wi-Fi networks.
Once connected to such a network, the offender is able to intercept and modify communications between the person using the network and, for example, the site to which you are connecting.
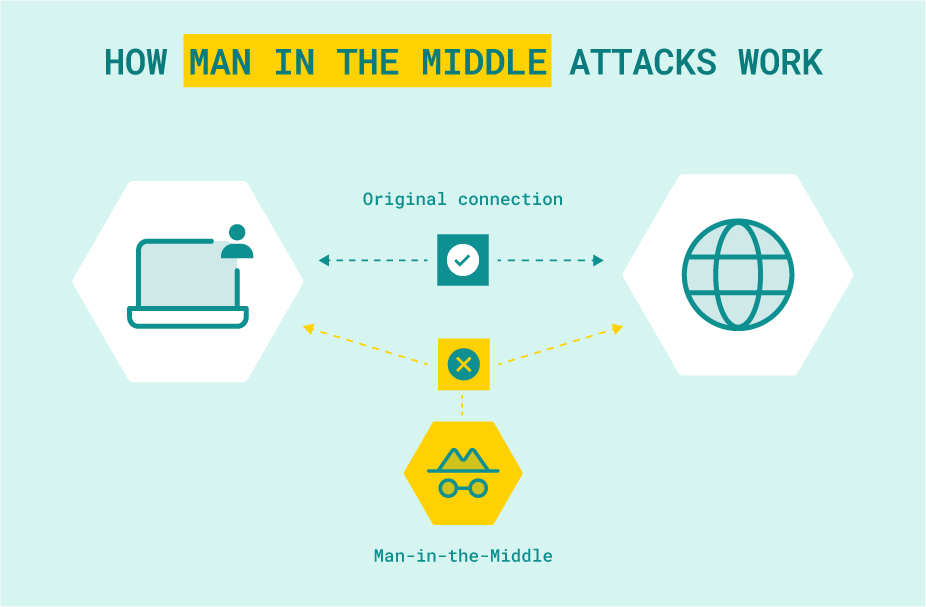
MITM requires placing an attacker or specific malicious tools between the victim and a targeted resource, such as the victim’s website or email program.
At first it is worth explaining that Captive portal is a page which appears to newly connected Wi-Fi users. On this page, sometimes you need to log in, and sometimes you just have to accept the terms and conditions.
If you “copy” a real Wi-Fi network with a captive portal where you have to be logged in, there is a possibility for Phishing, which I have written about in previous articles in the CyberLabs series.
Another way for an attacker to exploit a captive portal is to create one with malicious code that will try to take over our browser, giving new capabilities to an attacker.
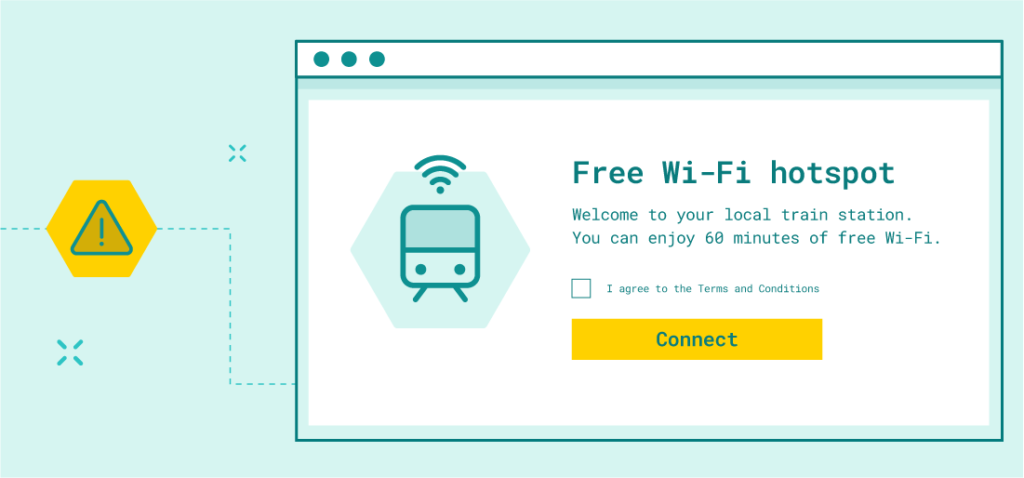
A captive portal is a website that is often displayed before accessing the Internet on public networks at airports, hotels or libraries.
As we can see, the two presented attacks can cause us a lot of problems, so it’s advisable to keep them in mind the next time we want to use a public Wi-Fi network.
However, these are not the only threats we are exposed to while traveling…
Maximize your email deliverability and security with EmailLabs!
It may seem that the cord you just borrowed to charge your phone is nothing more than an ordinary one, and the flash drive you found on the sidewalk may contain data about the person who lost it, so some of you will probably plug it into your computer to see what is on it (if only out of human curiosity).
If we do this, and the whole situation is not a coincidence, we can expect computer infection or data exfiltration. Such devices these days can be bought by anyone for little money, so the chances of an attack are much higher. However, the devices that can be potentially dangerous are worth knowing:
This group can include such devices as MalDuino, Rubber Ducky and Bash Bunny. Those are devices that look like ordinary flash drives, but when plugged into a computer, they perform pre-set actions such as downloading and running malware.
Some such tools can also be remotely controlled and send various commands in real-time to a device. More importantly, they are not recognized as storage devices but as keyboards, which means that USB port blocking (which usually involves detecting devices that are storage) will not work in this case.

Once connected to an attacked computer, BadUSB can discreetly execute malicious commands or inject malicious payloads.
These are cables with the help of which we can, of course, charge, for example, a phone or transfer some data. However, inside is an implant by which the cable performs certain actions as described in the previous example.
Some of today’s laptops do not have an input for an Ethernet cable. Network adapters come to our aid. However, there are adapters that, when connected, will give remote access to a device of an attacker. It is rather unnecessary to explain here the consequences that can follow this incident.
Cybersecurity threats, however, are not the only dangers that can lurk on us. Travelling, particularly during the upcoming holidays, is also a time when we experience increased luggage thefts, bags, etc.
Obviously, it may happen that we will simply forget to take, for example, a backpack from a restaurant. When we will return to the restaurant, we may already find out that our property has disappeared. If phones or laptops are stolen, this can lead to serious data leaks. Thus, it’s worthwhile to secure ourselves in advance properly.
Clearly, I mean securing our devices so that third parties do not have access to our data when stolen.
So it’s worthwhile to protect ourselves against this in advance at every step properly. Of course, I’m thinking here of securing our devices so that after theft third parties do not have access to our data, with help here comes software that we can install on a computer or smartphone.
This is probably one of the basic security features we should use in all devices or external storage. Thanks to encryption, our data will be secured appropriately. For encryption, we can use either the BitLocker software available for Microsoft systems or the VeraCrypt software.
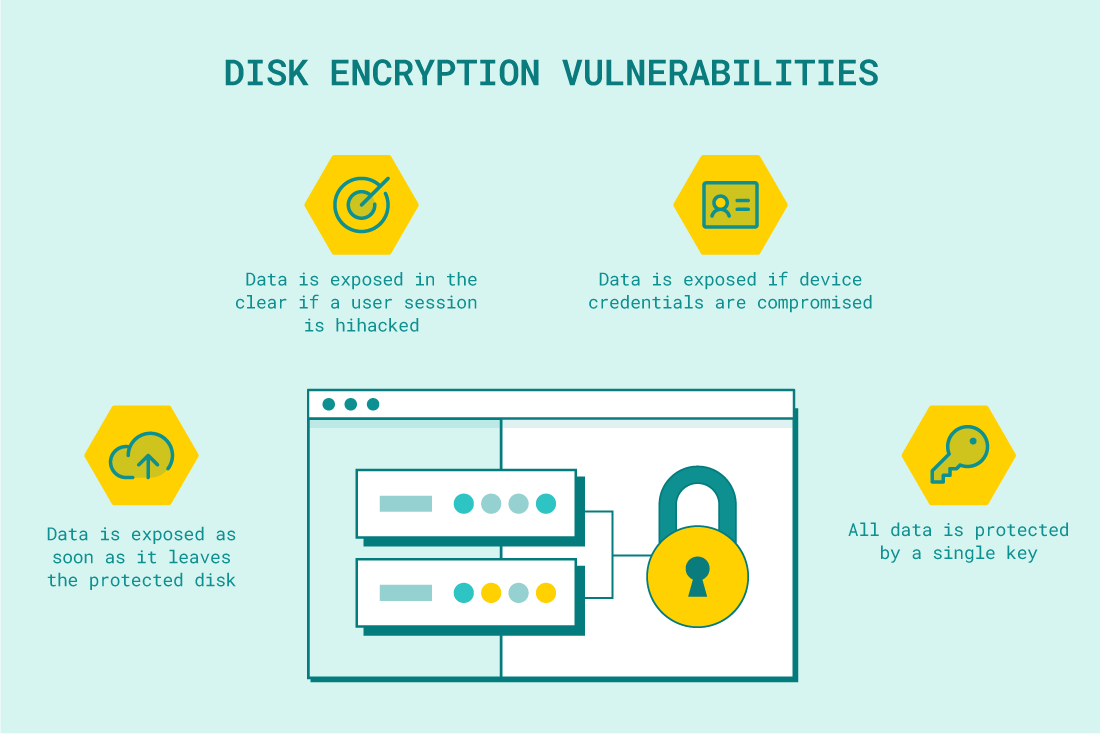
Security vulnerabilities allow hackers to gain access to the drive and copy data without the need for a password.
If someone gains access to our computer, make sure that passwords are not kept in a notepad. Hence, we should use password managers, which are safe for our passwords and additionally support 2FA so that they are even more protected. While using a password manager, avoid saving passwords in the browser.

Two-factor authentication is one of the best ways to protect against phishing, social engineering and authentication theft.
During travels, especially the longer ones, we have a lot of time, which somehow we want to spend. In such situations, we usually reach for our phones, tablets or laptops, either for work or simply “Internet browsing”.
We usually don’t want anyone to look into our devices and see what we are doing. However, I’m sure, more than once, you’ve noticed people who simply showed everyone around them what they’re actually doing on their devices.
In the previous article of CyberLabs series, I brought up the topic of social engineering and how a professional social engineer can manipulate us.
My advice is to sit in public places, if possible, in a way that prevents someone from standing behind you. In such situations, the filter will not work. Nonetheless, it is worth having the mentioned filter on your screen.
Maximize your email deliverability and security with EmailLabs!
In a previous article in the CyberLabs series, I zoomed in on the topic of social engineering and how a professional social engineer can manipulate us (Social engineering or hacking people’s minds).
In terms of travel, techniques of social engineering attacks can focus mainly on trying to convince us to lend a laptop or a phone under some excuse. If we agree to this, and on top of that, we won’t look at our devices, we can either end up losing the equipment through a physical theft, or in a short period of time, our device can be infected as well, or specific data can be exfiltrated (such as a password file).
Nowadays, when we pay for practically everything either by card or by online payments, we are exposed to the risks of skimmers. The skimmers can be divided into two types:
These are overlays on various elements of ATMs, payment terminals that are designed to read data from cards. Often they are glued very quickly so they can be “ripped off” without much difficulty. Therefore, it’s worth to take a look before withdrawing money from an ATM, if any elements look suspicious (e.g. card entry coming off).
Usually such skimmers are used in fake online stores, but they can also appear on real websites that have been taken over by cybercriminals. This is usually a malicious JavaScript code that takes the card data we provide and sends it to a server controlled by the offender.
If possible, do not use public Wi-Fi networks, instead, you can create your own hotspot (plus remember to hide its name – SSID).
When travelling, it’s a good idea to bring your own adapters, charging cables, etc. However, if we need to someone else e.g. cables, in such case borrow them from trusted people.
Flash drives of various kinds can be purposely distributed. Here the attacker is counting on our curiosity which will lead to connecting such a device to your computer. Under no circumstances should we do this if we do not know the source of the device.
Don’t leave your luggage unattended. Ladies who use handbags should remember to put their bags on their shoulders and keep them close. If we carry backpacks, make sure to wear them on both shoulders. Such behaviour will definitely make it more difficult, e.g., for our belongings to be snatched.
Let’s remember to encrypt our data! Once the devices with our data are stolen, a third party will not be able to access the information stored there easily.
Use the privacy filter on our laptops. Such filters are mainly useful when working in public places where a lot of people can look at our computers.
Before withdrawing money from ATMs, verify whether the device looks suspicious. You can also try pulling, for example, the part where you insert your card.
With online skimmers, it’s worth paying attention to whether you actually shop on trusted sites; if you own such sites, it’s worth conducting regular penetration tests aimed at finding as many bugs as possible that could be exploited by a cybercriminal precisely to embed an online skimmer.
Stay Secure! 👾
We live in a world where your customers switch seamlessly between laptops, smartphones, and tablets. They navigate a complex digital ecosystem – checking emails, using mobile apps, and reacting...
We are delighted to announce that Vercom S.A., the company behind the EmailLabs project, has successfully completed the ISO 22301 certification process. This significant achievement underscores our commitment to...
EmailLabs, as part of the Vercom group, proudly announces its full commitment to aligning its ICT services with the latest cybersecurity standards. In response to dynamically changing regulations, the...
We are pleased to announce that MessageFlow, a product from the Vercom S.A. group, has received the prestigious CSA (Certified Senders Alliance) Certification. This recognition not only underscores the...
Best practices, Maile marketingowe, Marketing E-mails, Transactional Emails
Mass email sending is a critical strategy for business owners, marketers, developers, and nonprofit managers looking to scale their outreach. Whether you are announcing a new product feature, distributing...
Best practices, Marketing E-mails
Customer feedback is the fuel for business growth, but gathering it effectively requires more than just a list of questions. Email surveys remain the most direct channel for understanding...
Best practices, Email Marketing, Pytania i odpowiedzi
Mail merge combines a template document with data to create personalized communications. This technique saves time by automatically generating individualized letters, emails, and labels without manual entry. What Is...
Best practices, Maile marketingowe, Marketing E-mails, Transactional Emails
Mass email sending is a critical strategy for business owners, marketers, developers, and nonprofit managers looking to scale their outreach. Whether you are announcing a new product feature, distributing...
Best practices, Marketing E-mails
Customer feedback is the fuel for business growth, but gathering it effectively requires more than just a list of questions. Email surveys remain the most direct channel for understanding...
Best practices, Email Marketing, Pytania i odpowiedzi
Mail merge combines a template document with data to create personalized communications. This technique saves time by automatically generating individualized letters, emails, and labels without manual entry. What Is...
IT & Tech, Pytania i odpowiedzi, Technical
When an email travels from sender to recipient, it passes through several critical components of email infrastructure. At the heart of this journey sits the Mail Transfer Agent (MTA)...
Best practices, Deliverability, Google and Yahoo's Requirements, Pytania i odpowiedzi
The world of email marketing is constantly evolving, and leading mail service providers – Gmail, Yahoo, Microsoft, and Apple – regularly update their guidelines for senders. In recent years,...
Gmail, Google and Yahoo's Requirements
You might have noticed a new item in your Gmail sidebar recently – the “Manage subscriptions” tab, often flagged with a blue notification dot. While Google announced this feature...
IT & Tech, Pytania i odpowiedzi, Technical
Efficient email communication isn’t just about sending messages — it also involves integrating email functionality into your business systems and applications. Email APIs (Application Programming Interfaces) serve as the...
One of the most important yet often underestimated elements in shaping a company’s brand perception is the transactional email. In e-commerce, the design of such messages must be carefully...
Google and Yahoo's Requirements, Yahoogle
2024 brought fundamental changes to email marketing, introducing new, stringent requirements for senders. Since February 1, 2024, Google and Yahoo have started enforcing new deliverability rules, primarily targeting bulk...