We present the second part of our CyberLabs series on the very important topic of password security. Today you will learn how passwords are leaked, what to do to keep your login data secure and how to use unique passwords. Please read on!
Passwords are something we use every day. For us, they are crucial, as they’ve become the key to sensitive data we don’t share on a daily basis. That’s why cybercriminals care so much about them (they often gain access to passwords through phishing or by hacking into a particular system – the popular password leak). While in the first case a password, even a complicated one, will be shared with the attacker openly, during a data leak our password is hashed and the cybercriminal must recover it (and it’’s up to us whether he succeeds).
CyberLabs #1- Phishing as one of the most popular cyber threats
This headline for each of us should be a certain rule that we use while registering in the new system. We should use an account with a unique username and password. The best password is one that is not used for multiple accounts.
Plus, it’s worth considering at this point whether our existing accounts have the same password. If not – it’s worth changing it.
This principle is very important, as you may often hear that in a certain attack, the criminal managed to obtain a login and password with which he could later log into many systems.
This lack of cyber-hygiene is what makes it possible for a cybercriminal to take over many of the accounts we use quickly. Here with helps comes a password manager, which will remember all of our solid and complicated passwords allowing us to use them at any moment.
When a database containing our passwords is leaked, we often receive a message that tells us to change them immediately. This is, of course, a reasonable reaction, but worth knowing that passwords in databases are not stored in an open form (at least they should not – what form they are stored in depends on application developers). In databases, the information is stored as a hash.
To make a long story short, it looks as follows: the user provides his account password during registration, and after submitting the form, the password using a hashing algorithm is turned into a string of characters called hash (the hash for a given password is always the same, obviously using the same hashing algorithm such as md5).
The entire process is a one-way street, which means there is no possibility to reverse it (you can’t easily turn the hash into the password hiding underneath it). For us, it’s an important piece of information, which means during leaks the attacker doesn’t have our password directly, but only the hash that needs to be cracked or “recovered.” Depending on whether the attacker can recover our password in a reasonable period of time is crucial information for us since it determines if a cybercriminal gains access to our account.
Password recovery time is mainly influenced by the level of its complexity (such as how long our password is, whether it includes all kinds of characters, whether it’s a “generated” password or rather, e.g., our name + date of birth) – the longer and more complex the password, the harder it will be to recover.
Additionally, the security of passwords itself is affected by the hashing algorithm chosen by developers.
There are actually many ways the leak can occur. Looking at the leaks over the past few months, we can see recurring patterns. Many times it all starts with phishing of user identities and passwords or data spoofing of an employee with the help of which the attacker gains access to the company’s internal network.
Other leaks start with already forgotten systems, which were supposed to be available only for a while, and which after several years have a lot of vulnerabilities. While other security breaches start with passwords or API keys, which are available in public repositories.
For this reason, you shouldn’t wait for the attacks and start much earlier to carry out regular audits of our systems and create safe passwords containing random words or other hard do brake strings of characters. Also, remember that often the attack starts with the “manipulation” of an employee, so let’s also conduct proper training or controlled phishing attacks, which will significantly sensitize employees.
As I mentioned, the password recovery time from the hash is greatly influenced by the level of password complexity. However, to understand why this is so important, you must know what methods cybercriminals use to recover a password from a leaked hash.
At first, though, it should be said that password recovery involves generating a huge number of hashes from certain strings of characters and comparing them with the original hash (that is, the one we want to crack). If hashes are the same, it will mean that we have found the password we are looking for.
In this case, the attacker relies on a so-called dictionary, which contains, for example, popular passwords (from other leaks), names, common names, etc. When recovering a hash with this method, a single word from such a dictionary is taken, and then a hash is generated from that word and compared with the hash we want to recover. The attack will succeed if our password is a common string such as Password. Of course, the attacker can create a password from several dictionaries. So if one dictionary contains the word “Strong” and another “Password,” the cybercriminal will also check the hash for the password “StrongPassword”
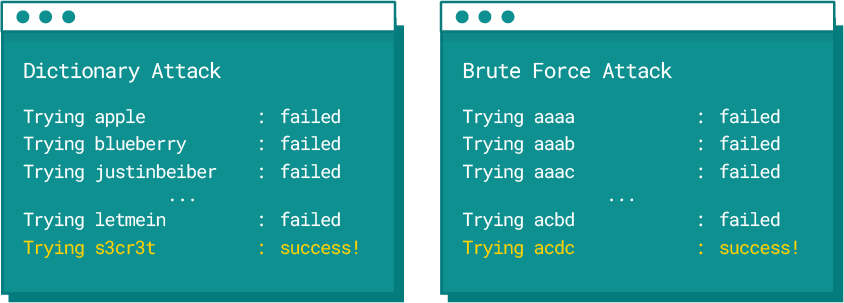
Dictionary attack vs brute force
The above methods can be successfully combined so that the cybercriminal can more effectively recover passwords from hashes gained through, e.g., a leak. While reading about password recovery methods, we may come to a fairly simple conclusion.
Our passwords cannot consist of simple words, as it will be possible to recover such a password using dictionary methods.
What’s more, as long as we use predictable passwords, where a particular type of character will be in specific places, e.g. the mentioned password with a capital letter at the beginning and numbers at the end, the attacker will be able to crack it in a reasonable time as well, since the character layout is quite predictable and commonly used.
All we need to do first is ensure we don’t have a weak password. Firstly password should be long (a minimum of 15 characters), and secondly, it should contain every kind of character in random places. An example of this kind could be, e.g. a password generated on a website available on the Internet:
6nA27x7#2W8!k&g
Such a password won’t be found in any dictionary of course. Moreover, the attacker will not be able to determine the location of specific characters.
Even if a cybercriminal finds that our password has 15 characters, he will be left to check all possible combinations made up of all potential characters (about 90) on each of the available 15 places. That results in many combinations which a cybercriminal won’t be able to check in a reasonable amount of time.
In the previous section, the information was presented, which clearly states the safest way is to use long (min. 15 characters) passwords consisting of all kinds of characters in random places.
The only “downside” of such passwords is the potential problem of remembering them. Plus, if we follow the rule: “one password, one system,” we may find that we have numerous passwords that are not easy to remember. Here, with the help comes Password Managers, a special safety locker for our passwords. Thanks to them, you don’t have to remember each password.
An example of such secure storage might be KeePassXC, which has a free version. This solution creates an encrypted digital vault for your passwords. Such password vault is kept locally on your computer. Access to this safe is protected by a master password (the only one we need to remember), so it’s worth making it strong enough.
Also, such a Password Manager can be secured with a hardware key, which we” ll discuss later in the article. Thanks to password management, we may keep our passwords protected (since we have a place where we can store passwords, we might as well generate passwords longer than 15 characters – this, of course, will only benefit our security).
KeePassXC is an open-source manager that is available for various systems and that we can integrate into the browser.
Certainly, KeePassXC is not the only one of its kind. We can successfully find other applications on the Internet. Most password managers additionally have plug-ins that we can install in the browser so we don’t have to enter passwords each time. For example, while logging in to Google, others have an application for a mobile device.
There are many password managers on the market, it all depends on our needs and we’ll certainly find a solution that satisfies us.
Two-factor authentication (2FA) is an additional security feature for user accounts during the login process for an individual social media account. When signing in, a login and password are still required; however, on an account with two-factor authentication enabled, you must provide an additional “ingredient” such as a code from a relevant app.

Two Factor Authentication (2FA) can help protect your online accounts, even if your password is stolen.
When deciding on two-factor authentication, we must consider which additional user authentication method to choose. Depending on the specific application, the number of available authentication methods may vary, but we will still have a choice:
If we choose this option while logging into our account, we receive an additional one-time code sent to our phone number provided during setup.
This method is very similar to the previously mentioned SMS code. Still, in this case, the code is generated in a special application, which we need to install on our mobile device earlier, while the app itself must be “linked” to our account. Generated codes are available for 60 seconds, after which a new code will be created.
This is the most secure method of two-factor authentication. While codes from the previous two methods can be obtained through phishing, using this method, we must physically plug the dongle into the USB port when logging into our account. Without this step, we won’t be able to log into the account!
Definitely yes! Two-factor authentication will significantly affect the security of your accounts. If the previously mentioned leaks of databases containing your passwords occur, using two-factor authentication effectively makes it more difficult for an attacker to access your account.
For that, if we use strong generated passwords, our account can be really well protected.
Apply the rule: “One password, one system”. Use multiple passwords. By taking care of password hygiene, even if an attacker is in possession of our password (whether through identity theft or by recovering the password from the hash), he will only be able to use it for one system thus significantly reducing the attack surface. Remember, using existing passwords can cause data breaches.
Use two-factor authentication, at least for the online accounts that are more important to us (the ideal situation is one in which we use 2FA on every account). If a similar situation as above occurs, i.e. our logins and passwords are taken over, the attacker won’t be able to log into the account. Remember that 2FA or other multi-factor authentication codes can be acquired during a phishing attack (identity theft), so be careful where you enter these codes!
To create passwords, it’s worth using so-called password generators, through which we can create an appropriate long, complex and unique password for us. This will help to resist attempts to break or recover them. Such security solutions are stopping us from creating weak passwords.
Don’t store your passwords in text files or sticky notes. For storing all your passwords, remember to use special Managers such as KeePassXC or other password managers.
Some leaks we might not even be aware of. So occasionally, we should check at, e.g., https://haveibeenpwned.com/ to see if our e-mail address appears in any data breach. If we discover that it’s in a leak, we’ll be informed about the name of the website from which our data leaked. Additionally, the site will tell us what kind of data is involved.
Stay secure! 👾
Gmail has announced significant changes in the requirements for email senders to maintain a good reputation and proper classification of messages in user inboxes starting from February 1, 2024....
Vercom S.A. public joint-stock company to which the EmailLabs project belongs, has been assessed and certified to be compliant with the ISO/IEC 27001 and ISO/IEC 27018 standards. The Vercoms’...
The increasing number of phishing attacks each year, and the projection that this trend will continue to escalate, aren’t likely to astonish anyone. This can be attributed, in part,...
Out of all the things that can go wrong when sending out marketing emails, having your emails end up in the recipient’s spam folder is arguably the most dreaded...
Email Authentication, Security
DMARC is an email authentication protocol that is designed to give domain owners the ability to protect their domain from unauthorized use, commonly known as email spoofing. Spoofing occurs...
With the emergence of the Covid-19 pandemic, many brands have been challenged to adapt in a short period to the changed reality and new consumer attitudes. That meant reorganizing...
Have you ever sent an email in haste and immediately wished you hadn’t? It happens more often than we’d like to admit. If you ever find yourself in this...
One safe and easy way to keep track of your digital interactions is to save emails as PDFs. However, do you know the best ways to easily turn your emails into PDF files? In this article, we’ll look into the different ways you can do to turn your emails into accessible PDF files. Let’s start! Key Takeaways To save emails...
Sending large files online can sometimes feel like maneuvering through a maze with unexpected twists and turns. The frustration of hitting attachment size limits or dealing with slow uploads...
Have you ever sent an email in haste and immediately wished you hadn’t? It happens more often than we’d like to admit. If you ever find yourself in this...
One safe and easy way to keep track of your digital interactions is to save emails as PDFs. However, do you know the best ways to easily turn your emails into PDF files? In this article, we’ll look into the different ways you can do to turn your emails into accessible PDF files. Let’s start! Key Takeaways To save emails...
Sending large files online can sometimes feel like maneuvering through a maze with unexpected twists and turns. The frustration of hitting attachment size limits or dealing with slow uploads...
Are you a bit baffled by email protocols like IMAP, POP3, and SMTP? Have no fear – this article is here to explain it all. If you have ever...
In 2024, global providers like Gmail and Yahoo have implemented a series of changes, primarily targeting bulk senders. These changes, already in effect, are part of a continuous update...
In the face of dynamic technological advancements and increasingly sophisticated cyber threats, ensuring network security has become crucial. Dozen security incidents present a challenge that we cannot afford to...
Google and Yahoo's Requirements
2024 marks a turning point in the fast-paced world of email deliverability, as this is the year when Google and Yahoo updated their sender requirements. With the enforcement period...
Best practices, Email Marketing
B2B email marketing – it’s a term you’ve likely heard before, but what does it really entail? And, more importantly, how can it be done effectively? In this article,...
Deliverability, Sending Reputation
Email sender reputation is one of the most important factors that can determine whether your emails reach the intended recipient or not. So, what is the email sender reputation,...