
Cybercriminals are thriving in their attacks, using communication channels such as sms, push and email. Day by day, attacks aimed at obtaining sensitive information related to these channels are increasing. One might even be tempted to say this is the “scourge of today’s digital world.”
However, do we know what this increase is due to? As mentioned above, is it only related to the increased public interest in the channels?
The main reason why more and more malicious messages or notifications are coming in to steal information is that it’s much easier to access tips, tools and even entire platforms prepared to send phishing, mass sms/mms campaigns, etc.
These days, you don’t have to be a specialist in a particular field to become a cybercriminal. We can get all the knowledge we need for the right amount of money, and it will only depend on us which type of communication we choose to attack. To get to the source of these threats, all we have to do is enter the so-called darknet, where newer and newer platforms or tools for cybercriminals are put up for sale every day.
In the remainder of this article, I will present some of the most common threats and, at the same time, the topics discussed in the “hidden” part of the Internet to touch on more cyber security information in the process.
Phishing these days is one of the most common cyber threats. It is also the primary initial vector that criminals use to get into, for example, a company’s network or employee accounts. Not surprisingly, it is also one of the more prevalent issues among criminals. Therefore, a platform called “Phishing as a Service” was created some time ago. Once you buy access to this platform, you get your instance, which has several modules:
Let’s illustrate phishing as a service with an example:
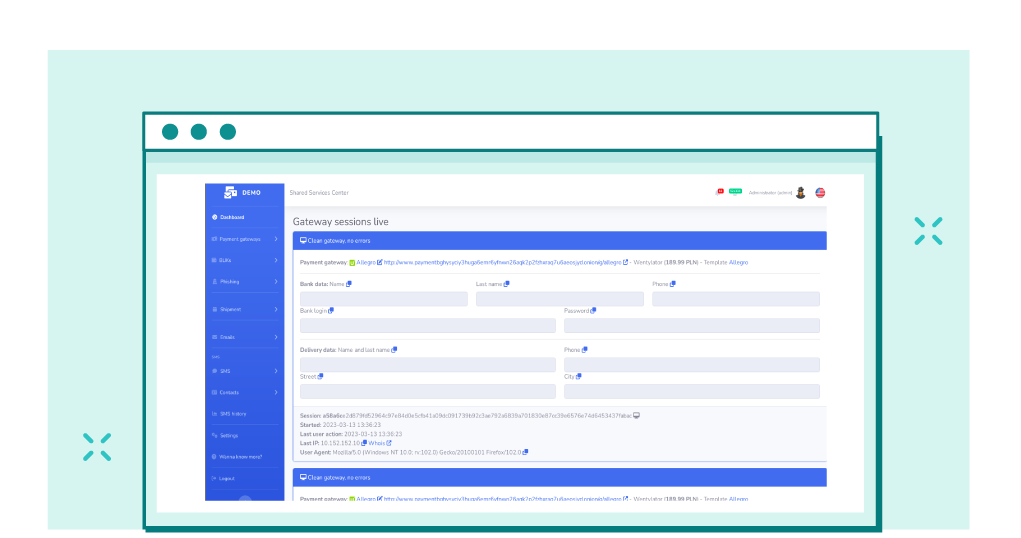
Administration panel for a system used to phish BLIK codes, and passwords, among other things.
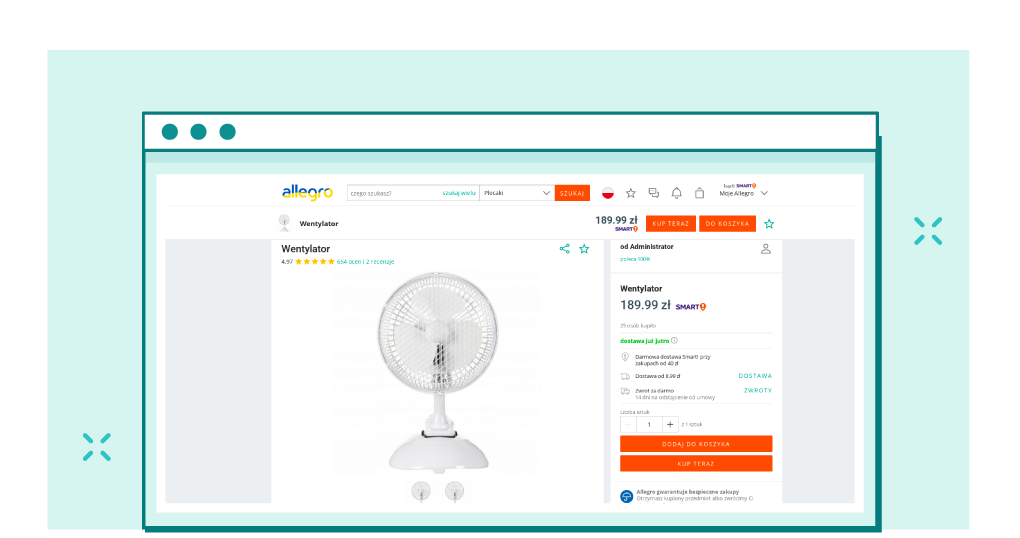
This offer was created by a previously shown administration panel, imitating a well-known Polish online auction and shopping website.
Thus, it is a very convenient and simple tool which does not need to be configured or secured in any way, as you get a ready-made solution after purchase. However, someone prefers to have more control over the platform. In that case, he can easily find popular payment gateways on various forums, along with tutorials discussing installing and configuring such gateways. They immediately have a special administration panel that allows you to copy, for example, Blik codes or use the acquired bank login data on the fly.
Maximize your email deliverability and security with EmailLabs!
Often paired with phishing messages goes Email Spoofing. This is an attack in which the attacker sends messages from an email address identical to the person they are impersonating.
During some attacks, cybercriminals study the target of their attack very carefully to lull the recipients’ alertness. They use appropriate language and add characteristic data/phrases.
How does the communication channel work here? In this case, one difference is the server from which the messages were sent. Another difference can be the Return-Path and Reply-To header, which can also be spoofed. Still, often the addresses in these headers are very different from the address from which the message came so that we can recognize spoofing. We can find information about the server as well as a lot of other helpful information when we view all message headers – depending on the mail/email client used, the steps may differ.
However, for less technical people, the message will look identical to the one sent from a natural person or a given organization. As in the previous example – the attacker does not need to configure his mail server. He needs to use one of the many free, publicly available tools.
Let me explain.
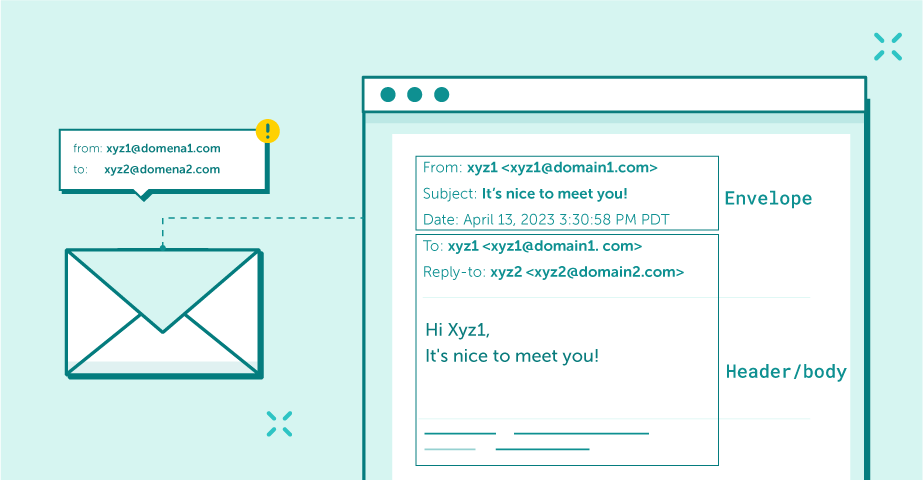
An example of a valid email message
The first rectangle represents the “envelope” field of an email message. Usually, these fields are automatically filled in for the sender when translating the header. Therefore, neither the sender nor the recipient usually sees this information. The elements in the second rectangle are the header and body. These are the sections you typically see when you open an email sent to you.
The sender can make changes to the message header and impersonate the sender’s identity so that the email looks like it came from someone other than Xyz1. Let’s go back to our example.
Let’s say you have a friend who is very fond of making all sorts of jokes, and you have just received an email from him with the following content:
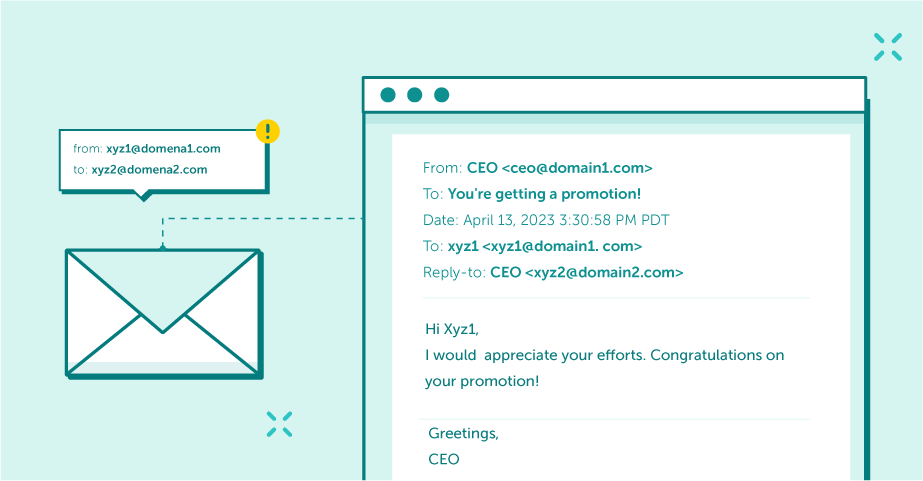
An example of email spoofing
Note that the “envelope” field is correct, but the “from” and “reply” fields are false. When Xyz1 receives this email, he may think it is from his boss. When he clicks “reply to,” he will only see the name “CEO” in the “from” field, but the message will go back to his colleague who forged the email, Xyz1.
In the same way, cybercriminals can cleverly disguise an email and customize it for their victims. For example, if a criminal wants to obtain banking information from his target, he can do the same thing as Xyz2. Still, instead of telling Xyz1 that he got a promotion, he can misrepresent himself in the email as a trusted bank and direct the recipient to go to a fake website.
The aforementioned records will allow us to increase the security of our email addresses because, with the correct configuration, an attacker will not be able to spoof our addresses. In addition, correctly configured records will increase the “rating” of our message which will allow it to bypass the “SPAM” folder.
However, what are these mysterious records?
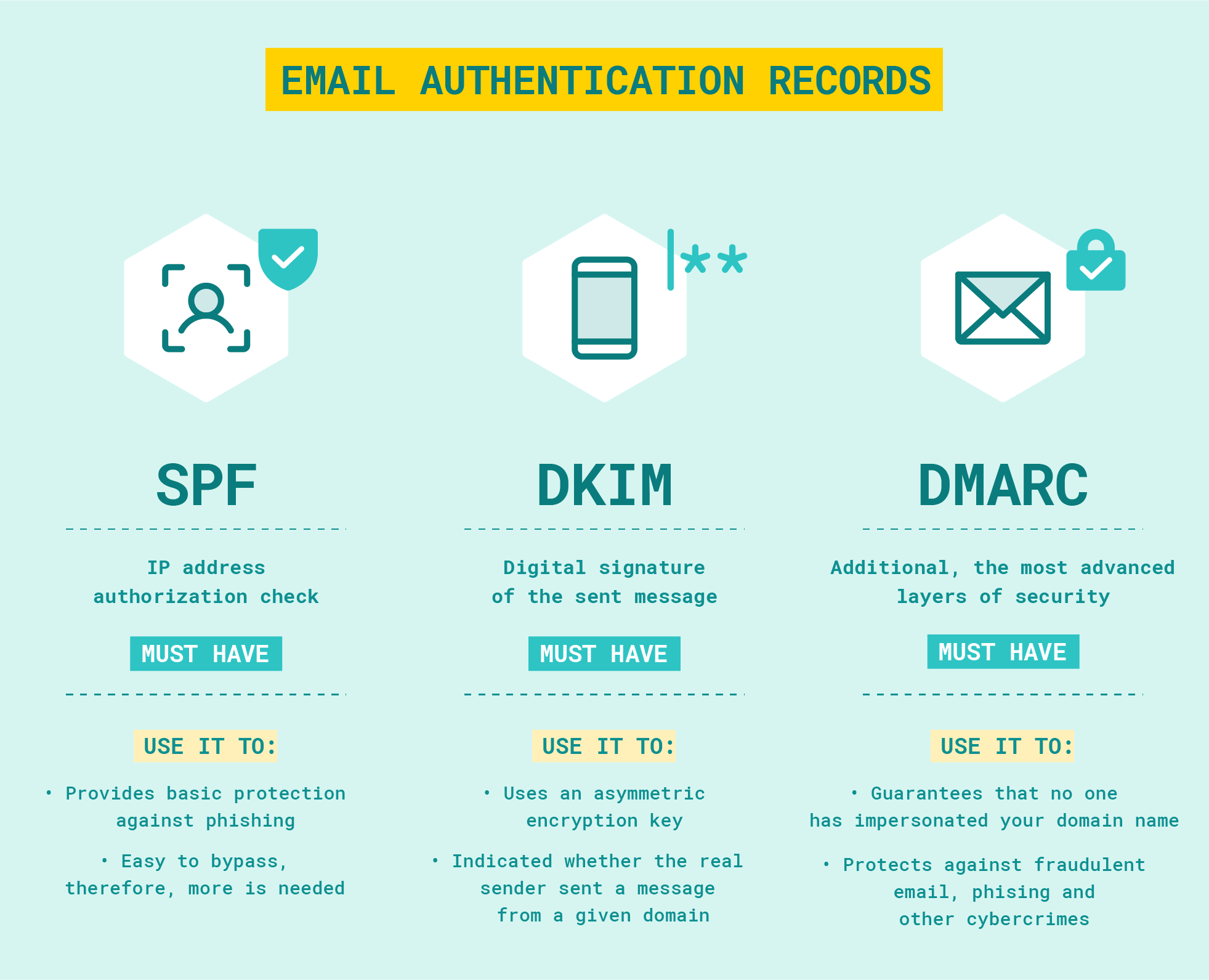
SPF, DKIM, DMARC: Basic elements of email authentication
Using SPF and DKIM alone will protect against people who want to impersonate our email addresses. It is also slowly becoming standard to implement a DMARC record, which will allow us to define what the server receiving the mail is supposed to do within unauthorized emails.
If it properly activates all these mechanisms and we add the appropriate records to the DNS, then, in addition to the fact that we will be more resistant to various attacks, we will further increase the deliverability of our campaigns.
To verify whether our emails have the records as mentioned earlier configured, you can use our entirely free MailChecker tool.
Any company that sends an SMS message after, for example, sending a request for a one-time code, signing up for a newsletter or other, can be vulnerable to this attack. This attack involves sending SMS messages in bulk to set phone numbers consecutively. It is caused by a need for proper monitoring on the server side, which accepts requests to send messages.
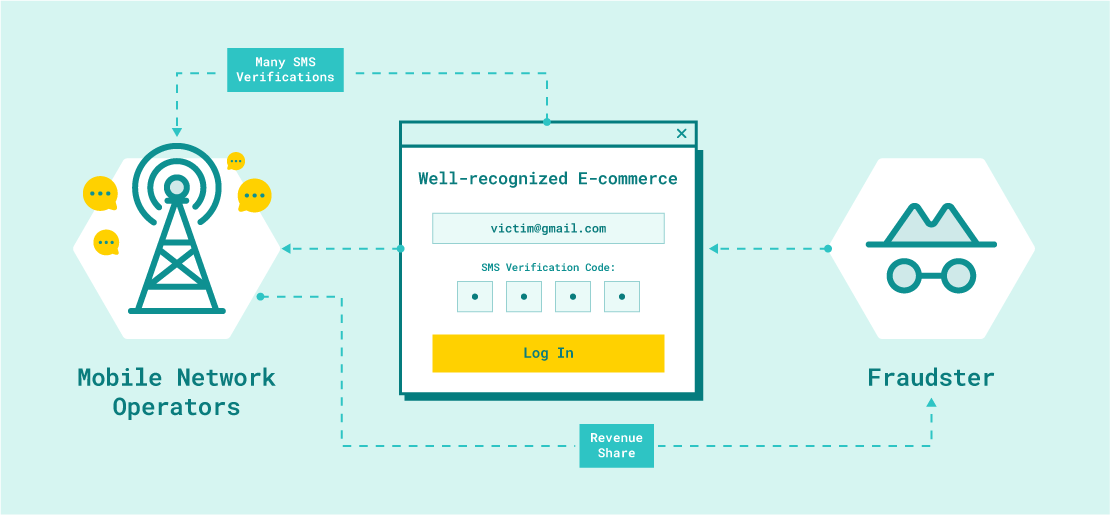
The scammers reap a portion of the income generated in this way, but the account owner foots the bill.
As we know, a professional social engineer can extract information from a person. Usually, during a conversation, we are very skillfully manipulated to give the attacker information that is important to them.
However, acquiring such skills requires many years of practice, and, in addition, not everyone can become a social engineer. Therefore, we can find many advertisements on the darknet, thanks to which we can order calls to any phone number, during which such a social engineering attack will be performed.
Of course, depending on the amount, the call can be made by an automated machine or by a natural person calling from a number that has a fake sender name. The whole thing can thus look like a call from, for example, a bank.
Maximize your email deliverability and security with EmailLabs!
In recent months, we have seen an increase in malicious campaigns using the push channel. However, all these campaigns can be divided into two types:
In both cases, it can all start with malvertising (using advertisements to spread malware) or with PDF files injected into malicious sites, in which we can find a so-called “fake captcha”, after clicking on which we are redirected to different places. During this, we are asked to consent to push notifications.
Once we agree, we will start receiving scam notifications. At this point, depending on the cybercriminal’s assumptions, we may be redirected to sites with fake stores where we can buy something at a steep discount (in reality, it’s a site with a so-called online skimmer that aims to defraud our payment card data).
Another scenario can look very similar to the previous one. Still, in this case, the push notifications impersonate Windows Defender, for example, and inform the victim that the computer is supposedly infected. By forcing us to fear losing, for example, data, we are forced to download a fake Windows Defender update that is supposed to get rid of the malware. In reality, we download malware that, once installed, will start stealing data from our computers.
As threats evolve, newer and newer security features must be implemented. However, it is essential to remember those cybercriminals can bypass any security over time, so an important part of the fight against threats is constantly improving one’s systems.
We can eliminate some threats by approaching them with an “open mind,” i.e. don’t allow ourselves to be manipulated, verify links/attachments from suspicious emails, etc. Other safeguards need to be implemented in our systems, and it is two such safeguards that we could read about recently.
We are, of course, talking about BIMI.
Brand Indicator for Message Identification is a method of enhancing the security of email communications that allows a logo of a company’s choice to appear right next to a message in the mailbox. However, requirements must be met for such a logo to appear in the message list.
Why does your company need BIMI?

BIMI is an extension of the existing standards (SPF, DKIM and DMARC) to include brand identity.
Sender Verification is a solution that allows you to authorize sender addresses among email providers such as Gmail, Onet, WP/O2, etc. When implemented correctly, a green shield will appear next to the sender’s name, which informs the recipient that the email has been verified. This means they are authorized to send messages from the given address.
Using these two safeguards allows many users to distinguish fake messages from real ones. As a result, this will translate into the number of messages opened. In addition, our addressees will be reassured that we also care about their security.
Stay Secure! 👾
We live in a world where your customers switch seamlessly between laptops, smartphones, and tablets. They navigate a complex digital ecosystem – checking emails, using mobile apps, and reacting...
We are delighted to announce that Vercom S.A., the company behind the EmailLabs project, has successfully completed the ISO 22301 certification process. This significant achievement underscores our commitment to...
EmailLabs, as part of the Vercom group, proudly announces its full commitment to aligning its ICT services with the latest cybersecurity standards. In response to dynamically changing regulations, the...
We are pleased to announce that MessageFlow, a product from the Vercom S.A. group, has received the prestigious CSA (Certified Senders Alliance) Certification. This recognition not only underscores the...
Best practices, Maile marketingowe, Marketing E-mails, Transactional Emails
Mass email sending is a critical strategy for business owners, marketers, developers, and nonprofit managers looking to scale their outreach. Whether you are announcing a new product feature, distributing...
Best practices, Marketing E-mails
Customer feedback is the fuel for business growth, but gathering it effectively requires more than just a list of questions. Email surveys remain the most direct channel for understanding...
Best practices, Email Marketing, Pytania i odpowiedzi
Mail merge combines a template document with data to create personalized communications. This technique saves time by automatically generating individualized letters, emails, and labels without manual entry. What Is...
Best practices, Maile marketingowe, Marketing E-mails, Transactional Emails
Mass email sending is a critical strategy for business owners, marketers, developers, and nonprofit managers looking to scale their outreach. Whether you are announcing a new product feature, distributing...
Best practices, Marketing E-mails
Customer feedback is the fuel for business growth, but gathering it effectively requires more than just a list of questions. Email surveys remain the most direct channel for understanding...
Best practices, Email Marketing, Pytania i odpowiedzi
Mail merge combines a template document with data to create personalized communications. This technique saves time by automatically generating individualized letters, emails, and labels without manual entry. What Is...
IT & Tech, Pytania i odpowiedzi, Technical
When an email travels from sender to recipient, it passes through several critical components of email infrastructure. At the heart of this journey sits the Mail Transfer Agent (MTA)...
Best practices, Deliverability, Google and Yahoo's Requirements, Pytania i odpowiedzi
The world of email marketing is constantly evolving, and leading mail service providers – Gmail, Yahoo, Microsoft, and Apple – regularly update their guidelines for senders. In recent years,...
Gmail, Google and Yahoo's Requirements
You might have noticed a new item in your Gmail sidebar recently – the “Manage subscriptions” tab, often flagged with a blue notification dot. While Google announced this feature...
IT & Tech, Pytania i odpowiedzi, Technical
Efficient email communication isn’t just about sending messages — it also involves integrating email functionality into your business systems and applications. Email APIs (Application Programming Interfaces) serve as the...
One of the most important yet often underestimated elements in shaping a company’s brand perception is the transactional email. In e-commerce, the design of such messages must be carefully...
Google and Yahoo's Requirements, Yahoogle
2024 brought fundamental changes to email marketing, introducing new, stringent requirements for senders. Since February 1, 2024, Google and Yahoo have started enforcing new deliverability rules, primarily targeting bulk...