In the third part of our CyberLabs series, you’ll learn what penetration testing is and why doing it is important to ensure cyber security.
Almost every company has a web application that can be accessed from the Internet. It’s not uncommon for customers to log into their accounts through the same application to make purchases or perform certain actions. So it’s safe to say that these apps are a “collection” of lots of data and cybercriminals will sooner or later try to get to this information.
That’s why it’s so important to take up some security measures and make sure that our apps are prepared for various types of attempted attacks. So do we perform IT security tests or tests on the software we use to protect ourselves from hacking attacks?
CyberLabs #2 – Password security, the reason why you should create strong passwords
Penetration testing (or pen tests in short) is an activity by which the largest possible number of flaws and security issues are found in, e.g. web and mobile applications, etc., which can negatively affect the confidentiality, integrity and availability of processed data.
To put it simply, it’s security testing which involves finding as many bugs as possible that a cybercriminal could use to, e.g., take over user accounts, extract information from the database or even take over the server on which the application runs. Professional penetration testing is a very important point for any company that cares about cyber security.
However, pentests themselves, unlike attacks by cybercriminals, are performed by pen testers (also penetration testers) for a specific period of time for a specific range of applications. What is also worth being aware of is that pentest won’t detect all vulnerabilities. One reason for this is the limited time for such tests. Another could be the incomplete range of tests or the emergence of new vulnerabilities previously unknown (e.g. weaknesses in a particular version of the software that our application uses).
Maximize your email deliverability and security with EmailLabs!
It has become assumed that flaws found in the pen testing process tests are classified on a five-point scale. This scale defines the level of threat and the consequences of its use and the time in which the errors should be fixed.
A critical vulnerability, the exploitation of a vulnerability classified as critical, makes it possible to take full control of a server or a network device. Vulnerabilities that have been marked as critical should be fixed immediately.
A vulnerability with a high level of significance, the exploitation of this vulnerability allows access to sensitive information but, beforehand may require certain conditions to be met for practical use. Vulnerabilities classified as “high” should be fixed within a very short time after they are reported.
A vulnerability assessment is marked as a medium level of significance; the exploitation of this vulnerability may depend on various factors. This vulnerability usually allows access to a limited amount of data or to data of lesser relevance. The fix for this vulnerability does not have to be implemented immediately, but it shouldn’t be postponed either.
A vulnerability with a low level of significance, the exploitation of this vulnerability has little impact on security or requires very difficult conditions to meet. Fixing this vulnerability can be done when the app is updated with, for example, new functionality.
General recommendations or information points marked with info level are not security vulnerabilities. They do, however, indicate good practices that, if applied, can increase the overall security level of an application.
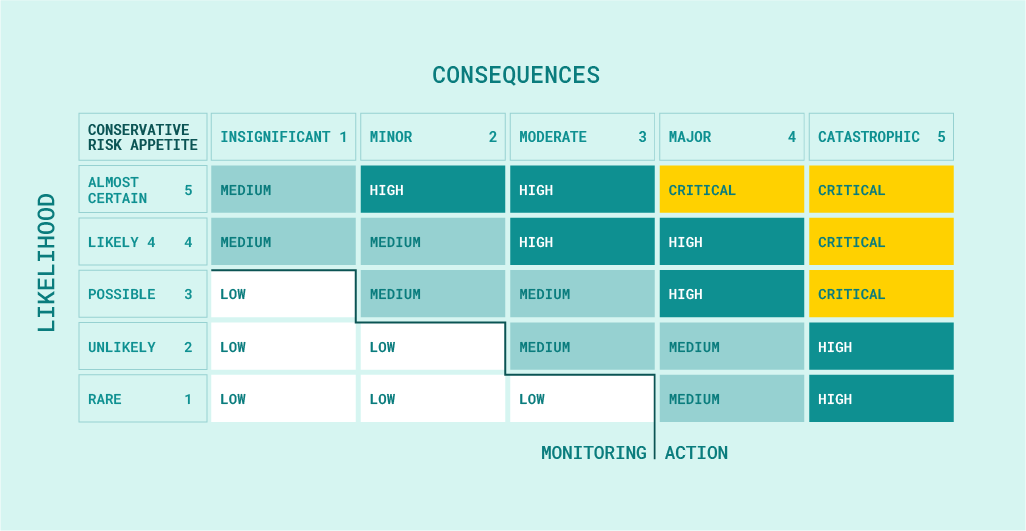
Classification of vulnerabilities
However, finding vulnerabilities is a major part of the pentester’s job, but that’s not the only thing the pentester does. After testing, it creates a report in which we can learn what vulnerabilities and weak spots were found in our applications.
In addition, at the end of the description of each vulnerability found, we will be able to read recommendations after applying, to which we can eliminate the vulnerability found. The pentester’s reports are used to evaluate the effectiveness of the applied security features based on the available types of penetration tests.
The ways to test an application can vary depending on the methodologies used. Holding to the following phases during testing will help us perform tests more efficiently. Looking at different methodologies, there are several main phases of testing. These include:
Once a vulnerability is found, e.g. SQL Injection vulnerability, the pentester may try to exploit vulnerabilities in order to gain access to the server. At this point, the tester may also try to escalate his privileges or exfiltrate specially prepared data (it’s important to determine during the phase in which we define the scope of testing whether the tester is to perform these actions).
After testing is completed, each test is summarized with a specially prepared report, in which we can find the listed vulnerabilities that were found and information on how to fix vulnerabilities.
The above phases are only a general “inventory” of each test, and in fact, each of the mentioned phases can be broken down into more specific points. Once the vulnerabilities found have been fixed, it’s worth performing a so-called Retest to verify that the vulnerabilities in question have indeed been eliminated.
Pentests can be performed according to their own methods, rules or principles however, there are proven methodologies and standards that are widely known among cybersecurity professionals and experts. Four well-known pen testing tools and standards are outlined below:
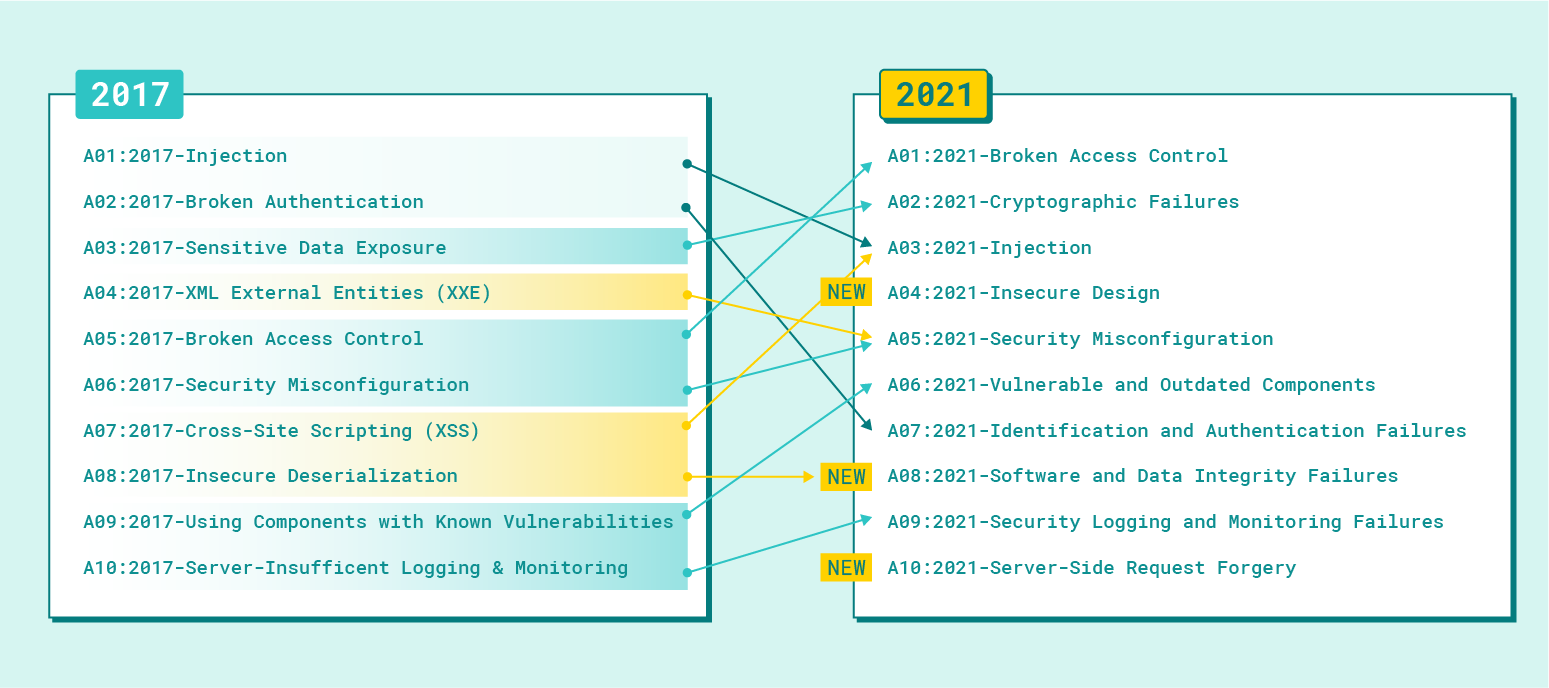
OWASP Top 10 is the standard document for developer awareness and web application security
Penetration Testing Execution Standard (PTES) –
The PTES methodology can be described as a mind map for the pen tester. Each element briefly describes issues from 7 main sections, including information acquisition, threat modelling, vulnerability analysis, exploitation or reporting.
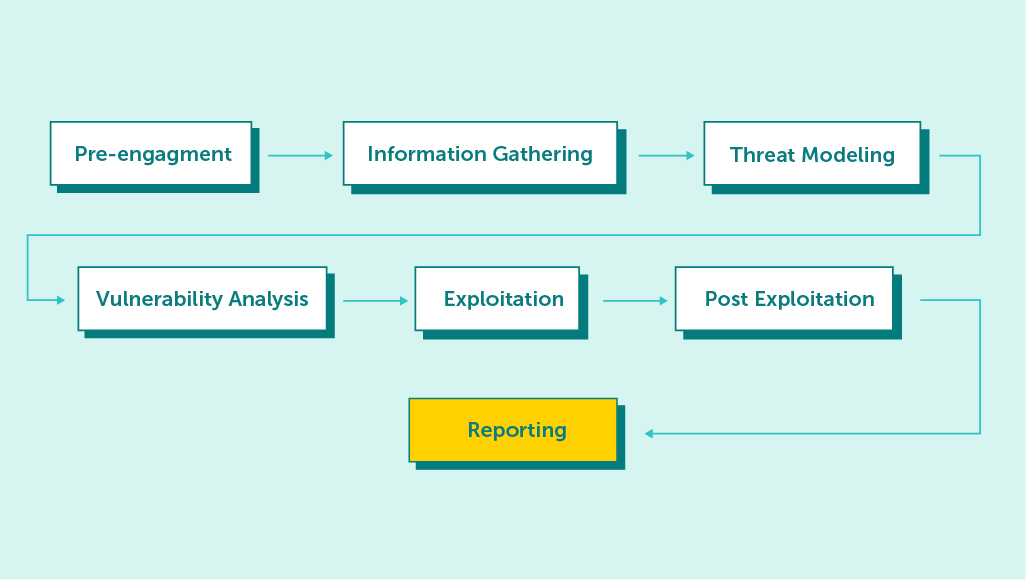
The goal of PTES is to provide high-quality guidance to help raise the bar for penetration testing quality.
Maximize your email deliverability and security with EmailLabs!
Depending on the type of system, or application being tested, the types of vulnerabilities may vary. It’s worth taking care of the application security itself from the earliest moments of software development and not only when it is ”mature“. This is because there is a chance that our software, due to vulnerabilities, won’t be able to be released to the public within the set timeframe, which may be associated with various negative consequences.
However, in order to be able to secure our applications and prevent data breaches properly, we should know which potential vulnerabilities we have to deal with. Below are some of the most common vulnerabilities in web applications.
Using XSS vulnerabilities, an attacker is able to embed malicious JavaScript code into a given application. Depending on the type of XSS, the attacker is able to, for example, modify the appearance of a page, run malware, steal session cookies or create new accounts with administrator privileges.
Using SQL Injection vulnerability (depending on its location), the attacker is able to bypass the login panel, and extract and modify the database. In critical situations, using this vulnerability, he’s able to read any file from the server or take over the entire server.
Many of today’s applications use a template engine. Still, not everyone knows that by exploiting this vulnerability, we can inject malicious code into the template, which will be executed either on the client or server side. Depending on where the code is executed, we can talk about XSS-like effects (the code executes on the customer’s side), or the cyber attack can even result in a server takeover (the code executes on the server’s side).
If our application is vulnerable to this flaw, an attacker can execute system commands on the server on which the vulnerable application is running.
With Path Traversal vulnerability, an attacker can read any file from the server (such as configuration files). When accessing application logs, there is a possibility to execute a Log Poisoning attack, in which our code is placed in the logs by means of an invalid SSH login (the code is usually placed in the username field). When this file is referenced, the code will be executed.
many other vulnerabilities can be put under this point because it really all depends on the vulnerabilities found in the software used. A very important element of a secure system is upgrading the software that our system uses. If for some reason, we can’t perform the update, it’s worth considering mitigating vulnerabilities to limit the attack field.
It’’s one of those vulnerabilities where the attacker doesn’t need to know much about hacking. A vulnerability of this type can, for example, occur when we go to our account settings, and in the URL, we see an ID for our account. If the application is prone to this vulnerability after changing the ID, we will see, e.g., details of another account.
The vulnerabilities above are, of course, only a part of what developers have to deal with because the list of security weaknesses is much, much longer….
Penetration tests are focused on finding as many vulnerabilities as possible in the indicated, e.g. web applications. Pentester, during such tests, sticks “rigidly” to its scope, i.e. to a specific app, and doesn’t link the found vulnerabilities into so-called cyber kill-chains, by means of which sensitive data could be intercepted.
Thus, these tests allow for checking whether a particular web application is secure. Still, they do not allow determining whether an organization is prepared for real cyber threats from hackers. The solution to this problem is Red Team testing.
Red Team tests differ from penetration tests in many ways. The most important differences are:
So you can sum up the differences between the tests as follows: penetration testing is a good solution for finding as many system security flaws as possible in a given system that need to be fixed. In contrast, red team testing provides an ideal solution when it comes to a company’s system’s defences against hacking attacks.
| PENETRATION TESTING | RED TEAMING |
|---|---|
| It’s a portion of red teaming focused on exploiting certain vulnerabilities of a system. | It’s a framework to evaluate the level of security of an organization. |
| The IT Team is aware of this exercise and takes part in the activity. | Only upper management knows a test is being carried out |
| It’s a small targeted attack. | It’s emulates a real-world situation. |
| It uses commercial pen test tools. | It resorts to social engineering and can even try enter the offices to test the physical security. |
As in previous CyberLabs – all you need to know about cybersecurity series articles, below you’ll find some good tips to increase the level of cyber security in your organization:
Stay secure! 👾
We live in a world where your customers switch seamlessly between laptops, smartphones, and tablets. They navigate a complex digital ecosystem – checking emails, using mobile apps, and reacting...
We are delighted to announce that Vercom S.A., the company behind the EmailLabs project, has successfully completed the ISO 22301 certification process. This significant achievement underscores our commitment to...
EmailLabs, as part of the Vercom group, proudly announces its full commitment to aligning its ICT services with the latest cybersecurity standards. In response to dynamically changing regulations, the...
We are pleased to announce that MessageFlow, a product from the Vercom S.A. group, has received the prestigious CSA (Certified Senders Alliance) Certification. This recognition not only underscores the...
Best practices, Maile marketingowe, Marketing E-mails, Transactional Emails
Mass email sending is a critical strategy for business owners, marketers, developers, and nonprofit managers looking to scale their outreach. Whether you are announcing a new product feature, distributing...
Best practices, Marketing E-mails
Customer feedback is the fuel for business growth, but gathering it effectively requires more than just a list of questions. Email surveys remain the most direct channel for understanding...
Best practices, Email Marketing, Pytania i odpowiedzi
Mail merge combines a template document with data to create personalized communications. This technique saves time by automatically generating individualized letters, emails, and labels without manual entry. What Is...
Best practices, Maile marketingowe, Marketing E-mails, Transactional Emails
Mass email sending is a critical strategy for business owners, marketers, developers, and nonprofit managers looking to scale their outreach. Whether you are announcing a new product feature, distributing...
Best practices, Marketing E-mails
Customer feedback is the fuel for business growth, but gathering it effectively requires more than just a list of questions. Email surveys remain the most direct channel for understanding...
Best practices, Email Marketing, Pytania i odpowiedzi
Mail merge combines a template document with data to create personalized communications. This technique saves time by automatically generating individualized letters, emails, and labels without manual entry. What Is...
IT & Tech, Pytania i odpowiedzi, Technical
When an email travels from sender to recipient, it passes through several critical components of email infrastructure. At the heart of this journey sits the Mail Transfer Agent (MTA)...
Best practices, Deliverability, Google and Yahoo's Requirements, Pytania i odpowiedzi
The world of email marketing is constantly evolving, and leading mail service providers – Gmail, Yahoo, Microsoft, and Apple – regularly update their guidelines for senders. In recent years,...
Gmail, Google and Yahoo's Requirements
You might have noticed a new item in your Gmail sidebar recently – the “Manage subscriptions” tab, often flagged with a blue notification dot. While Google announced this feature...
IT & Tech, Pytania i odpowiedzi, Technical
Efficient email communication isn’t just about sending messages — it also involves integrating email functionality into your business systems and applications. Email APIs (Application Programming Interfaces) serve as the...
One of the most important yet often underestimated elements in shaping a company’s brand perception is the transactional email. In e-commerce, the design of such messages must be carefully...
Google and Yahoo's Requirements, Yahoogle
2024 brought fundamental changes to email marketing, introducing new, stringent requirements for senders. Since February 1, 2024, Google and Yahoo have started enforcing new deliverability rules, primarily targeting bulk...