
Sociotechnic, or in other words social engineering, is any action that influences another individual in order to persuade him to take certain actions, which may not be in his personal interest. Often we can come across the statement that social engineering is mainly used by criminals of various sorts to impersonate a person, to trick a person into certain information or to manipulate another individual to perform a specific action. However, social engineering is practically with us every day.
Now you may think: “But how so?”, yet if you think carefully you will find the answers very quickly.
To explain the earlier statement saying that social engineering is used against us practically every day, you don’t have to look far. Take, for example, supermarkets.
Have we ever wondered why everyday products are actually placed all over the store?
The use of this simple trick forces us to walk through practically the entire store (even when doing a little shopping) which can result in seeing X more things along the way, things we take even though we don’t have it on the list.
Other examples of social engineering used against us can be newspapers, and advertisements where a product being promoted is praised by well-known people in whom we have a certain “trust”. We perceive such individuals as a sort of authority, so since a celebrity encourages us to buy a certain item, subconsciously we also need to own it. Never mind that basically, the same product may be even half the price, after all, it’s the product we heard about on TV that we must own.
Social engineers use the same methods of persuasion that we all use every day. We play roles. We try to be credible. We create mutual commitments. But the sociotechnician applies these methods in a manipulative, fraudulent, highly unethical way, often with devastating results.
Being therefore unaware of this manipulation, which is applied in our direction by the mass media and others, we are in fact defenseless. Thus, if we become the target of an experienced social engineer-criminal, the consequences of such manipulation can be terrible for us. Especially since these individuals know inside out the various techniques of manipulation, based on a carefully prepared identification of their target
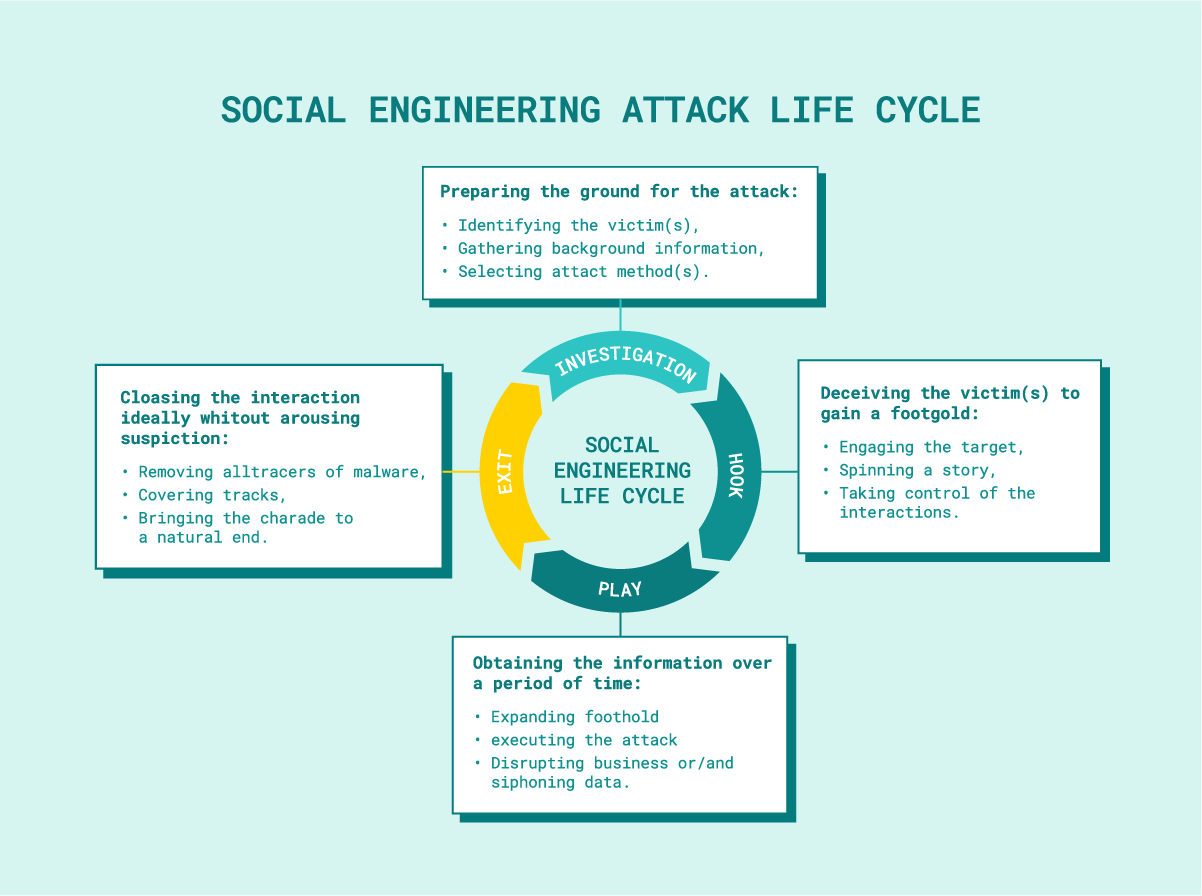
Social engineering attack life cycle
Maximize your email deliverability and security with EmailLabs!
While the manipulation of our minds, e.g. through marketplaces, is not directly harmful to us, the use of this weapon by a cybercriminal, e.g. in a direct conversation (when trying to invade a company physically) or through the use of phishing, smishing can be both for us personally and for company welfare a very “painful” and costly experience.
The answer is quite simple: because it’s easier.
The human factor is usually considered the most risky ( by its high unpredictability) in design of any security system, because, as it turns out, it fails most often. Humans by nature make decisions quickly, driven by intuition, based on the information they have just encountered, even if that information is incomplete or even false. Being rationally cautious and weighing the arguments “for” and “against” require an effort that we usually try to avoid. This is an evolutionary property that allows us to save time and brain resources for solving life’s most important problems.
Unfortunately, the intuition that allows us to make choices so quickly and automatically is a serious danger if we apply it out of convenience to important issues such as money, security or privacy.
As at the beginning of any attack, the offender must prepare and gather as much information as possible about the target as well as the victim, i.e. a person who makes possible to achieve it. For social engineering attacks, information about email addresses, phone numbers, the internal structure of the organization, the network of interrelationships or the private lives of employees can be useful (here a lot of information can be provided by social media).
These and many, many other pieces of information can be obtained using OSINT (open-source intelligence), which is the basis of social engineering. It’s a certain category of business intelligence that allows us to gather various data from publicly available sources.
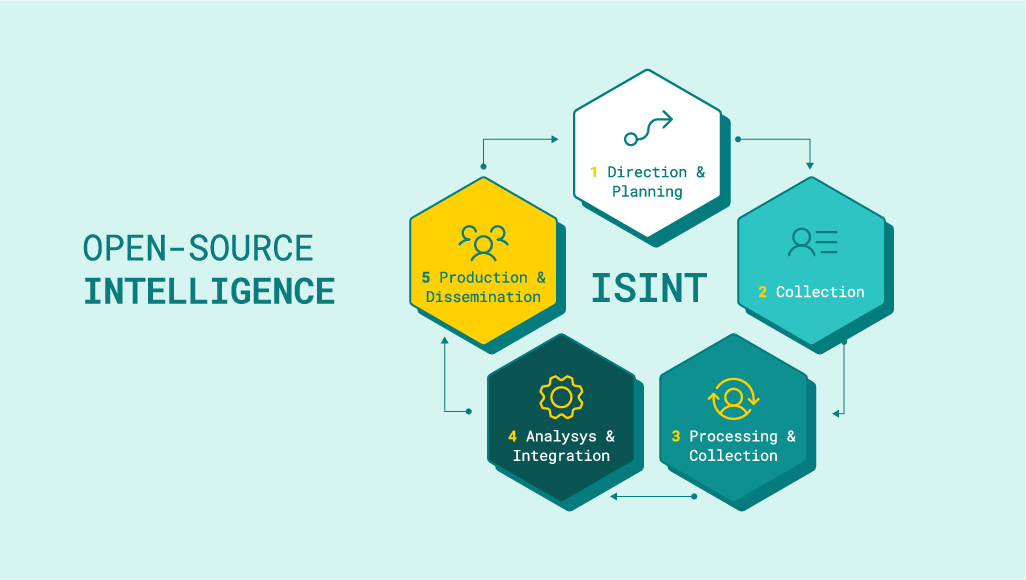
Open-Source Intelligence
Of course, simply sweeping through a huge number of sources can be quite time-consuming, so various services, mechanisms, tools come to our aid. A short list of OSINT capabilities is presented below:
People identification based on faces – it may happen that a photo of employees from, e.g., a team-building event is uploaded to the web. If such a photo is available on popular social media, it is enough to look through comments or so-called “likes” to try to determine the identity of specific employees and thus gain a lot of information about them that can be used in social engineering attacks.
However, what if the photo is available on a company website where we cannot follow the above? In this case, you can use special search engines that, based on the face photo, can find pages / accounts where the same or similar person appears (it must be remembered that this kind of search does not give 100% search accuracy).
GHDB (Google Hacking DataBase) – GHDB can be called an advanced Google search. Using special search queries, we can look for publicly available information. What kind of information is it? Here we can start with login panels, database backups, through files with passwords or “confidential” documents in the so-called deep cover. Besides, a cybercriminal can use GHDB to search for sites vulnerable to a specific security flaw.
There are entire books written on OSINT, so if this topic interests you, surely you’ll find something worthwhile. In fact, with the help of OSINT, we can profile selected people in a very accurate way and learn about them on many things whether it’s information related to work or personal life. Undoubtedly, all these details gained in the presented or other way, the social engineer will be able to turn against us.
Increasing volumes of online information are being used in data gathering and analysis. In addition, Western nations face shortages of data analysts coupled with an increasing demand for militarie AI. Data science in governmental sectors generally handles more complex projects, developing tools to support low-level analysts on intuitive systems. Intelligence teams have to face the challenge of not accessing the latest internet sources.
It is possible to download OSINT software for free or pay. It’s really impossible to have a solution that is 100% effective. Instead, integrating several different solution options would be the ideal strategy. Keep in mind that OSINT toolkits have geographic elements which can be seen through a digital window. Your tooling will depend upon your organisation’s needs.
Increasingly businesses are transforming their business strategies to embrace digitalization. The technology is beneficial in improving customer experience, productivity, and resources management. But in the same vein, the adoption of technology increases the possibilities of compromises.
The same holds true of almost all industries with a web presence, namely finance, retail, and transportation. Digital transformation can have significant implications on physical security as criminals use a more anonymous online medium.
Dumpster Diving is a method of OSINT used by various criminals to obtain a wide variety of information. Usually the interest falls on corporate containers in which it’s common to find leftover documents with names, phone numbers, email addresses, bank account numbers, logins or even passwords.
So it’s worth being aware that to an attacker, a potential saved piece of paper thrown in the trash can be a source of a great deal of information that can later turn to the company’s disadvantage.

Dumpster diving is a way for an attacker to gain information, which he uses to build trust.
Maximize your email deliverability and security with EmailLabs!
To be able to protect ourselves from certain threats, we need to know how they happen, what causes them. Therefore, in this part of the article we will look at some principles, techniques, rules that professional social engineers use.
The principle of reciprocity is based on the idea that people usually want to return a favor for various gifts, pleasures. Usually people who are given such gifts (even if it was unwanted) have a sense of “unpaid debt.” Taking advantage of this principle, a social engineer will first try to discover what his target particularly values in order to later use this information to the target’s disadvantage. What’s more, people are willing to perform certain actions after hearing, for example, a compliment ( a kind of pleasure I wrote about earlier).
The principle of commitment is very similar to the principle of reciprocity, which I wrote about a bit above. As a rule of reciprocity was the feeling of personal indebtedness after receiving, e.g., a private gift or other pleasure such as a compliment. Commitment, however, refers to social norms and the expectations that come with them. An example of the use of this principle could be a situation in which a socialite wants to walk through a door that is secured by card access.
The situation could turn out to be one in which the socialite tries to walk through the door with something heavy in his hands during busy hours, such as a cardboard box of documents. Social standards require you to hold the door for such a person and let him in. The situation may seem abrupt, however, you have to believe that such situations happen very often, all because we don’t want to come off as a rude person.
This is a fairly simple principle which states that if a person with significant authority says something or performs some action then people usually take it very seriously. A simple example would be a policeman telling us to stop. Probably 99% of readers would carry out this command without a second thought. Usually, authority is associated with people who are confident and look that way, i.e. these people have a puffed-out chest, have their heads raised and it’s unlikely to find any signs of fear or uncertainty on their faces.
Furthermore, authority often evokes confidence in us, so that we don’t require any proof to confirm why we should actually listen to a person. What’s important, this type of authority doesn’t have to come directly from us, a social engineer can use here, e.g. a fake text message from someone high in the company’s hierarchy, in which someone urges us to join an important meeting.
Social proof is a method that helps persuade others to do things they don’t want to do. This method may be more widely known as the sheeple effect. Usually when we are unsure of something, confused we pay attention to what others are doing to get an idea of what we should do in a given situation.
An example might be an elevator. If everyone in the elevator is standing facing the entrance with their back for sure you will sooner or later stand that way too. This is exactly how social proof works. A social engineer can use social proof in such a way that everyone else has already signed up for a given list and you haven’t yet. Of course, the alleged list will be malware.
I once read the phrase, “People like people who like what they like. They also like those who like them” which perfectly explains this principle. People who belong to one “tribe” have a sense of mutual closeness, familiarity which can make them trust each other. However, for a social engineer to use this rule, he must establish a certain relationship with the indicated target.
All this because the feeling of affection must be genuine (if we pretend to be friendly and the other person realizes it, we may lose the opportunity to manipulate them) besides, genuine non-verbal signals play a huge role here and can help to build trust. Once such a relationship has been built, a social engineer will be able to easily manipulate us into performing certain actions. Surely it has happened to you at least once to do some favor to a person you like.
Of course, the above principles, methods are only part of the “arsenal” that will be used against us by a professional social engineer. While during face-to-face conversations the above principles are more real, it may be hard for us to imagine how to apply them during, for example, a phishing attack. Usually, however, in phishing messages, a cybercriminal tries to evoke certain emotions in us, such as fear ( unpaid invoice resulting in ceasing to provide a certain service), euphoria (an alleged big win in e.g. a lottery) or embarrassment (alleged leakage of private messages).
Follow the clean desk rule. Social engineers are very observant people. When interviewing you, they will definitely pay attention to the documents left behind, which can be a valuable source of information.
Use special paper shreddes – if the documents contain confidential data, there are special companies that shred such documents. Let’s remember that once cut into strips, the documents can still be read! So let’s be careful when shredding and disposing of documents.
Be careful what you “upload” to the Internet, – a seemingly ordinary photo can cause a lot of problems (it’s worth paying attention to whether you see documents somewhere in the background picture, a launched computer, etc.).
Let’s not get carried away by our emotions and use common sense during, e.g., telephone conversations. So let’s not give confidential information to a person who claims to be a bank employee.
Stay Secure 👾
P.S. Did you see our last CyberLabs #3 – Penetration Testing – Identify flaws before a cybercriminal does?
We live in a world where your customers switch seamlessly between laptops, smartphones, and tablets. They navigate a complex digital ecosystem – checking emails, using mobile apps, and reacting...
We are delighted to announce that Vercom S.A., the company behind the EmailLabs project, has successfully completed the ISO 22301 certification process. This significant achievement underscores our commitment to...
EmailLabs, as part of the Vercom group, proudly announces its full commitment to aligning its ICT services with the latest cybersecurity standards. In response to dynamically changing regulations, the...
We are pleased to announce that MessageFlow, a product from the Vercom S.A. group, has received the prestigious CSA (Certified Senders Alliance) Certification. This recognition not only underscores the...
Best practices, Maile marketingowe, Marketing E-mails, Transactional Emails
Mass email sending is a critical strategy for business owners, marketers, developers, and nonprofit managers looking to scale their outreach. Whether you are announcing a new product feature, distributing...
Best practices, Marketing E-mails
Customer feedback is the fuel for business growth, but gathering it effectively requires more than just a list of questions. Email surveys remain the most direct channel for understanding...
Best practices, Email Marketing, Pytania i odpowiedzi
Mail merge combines a template document with data to create personalized communications. This technique saves time by automatically generating individualized letters, emails, and labels without manual entry. What Is...
Best practices, Maile marketingowe, Marketing E-mails, Transactional Emails
Mass email sending is a critical strategy for business owners, marketers, developers, and nonprofit managers looking to scale their outreach. Whether you are announcing a new product feature, distributing...
Best practices, Marketing E-mails
Customer feedback is the fuel for business growth, but gathering it effectively requires more than just a list of questions. Email surveys remain the most direct channel for understanding...
Best practices, Email Marketing, Pytania i odpowiedzi
Mail merge combines a template document with data to create personalized communications. This technique saves time by automatically generating individualized letters, emails, and labels without manual entry. What Is...
IT & Tech, Pytania i odpowiedzi, Technical
When an email travels from sender to recipient, it passes through several critical components of email infrastructure. At the heart of this journey sits the Mail Transfer Agent (MTA)...
Best practices, Deliverability, Google and Yahoo's Requirements, Pytania i odpowiedzi
The world of email marketing is constantly evolving, and leading mail service providers – Gmail, Yahoo, Microsoft, and Apple – regularly update their guidelines for senders. In recent years,...
Gmail, Google and Yahoo's Requirements
You might have noticed a new item in your Gmail sidebar recently – the “Manage subscriptions” tab, often flagged with a blue notification dot. While Google announced this feature...
IT & Tech, Pytania i odpowiedzi, Technical
Efficient email communication isn’t just about sending messages — it also involves integrating email functionality into your business systems and applications. Email APIs (Application Programming Interfaces) serve as the...
One of the most important yet often underestimated elements in shaping a company’s brand perception is the transactional email. In e-commerce, the design of such messages must be carefully...
Google and Yahoo's Requirements, Yahoogle
2024 brought fundamental changes to email marketing, introducing new, stringent requirements for senders. Since February 1, 2024, Google and Yahoo have started enforcing new deliverability rules, primarily targeting bulk...