
One of the most dire situations a business can face is unauthorized access to its company network. This breach can lead to the theft of valuable intellectual property and customer data, which might then be sold on darknet marketplaces.
This situation is often exacerbated by ransomware, a form of malicious software that encrypts as much of the business network as possible. It then demands ransom in exchange for decrypting the data, essentially holding our information hostage. Additionally, we must reckon with various penalties related to the breach of personal data, not to mention the significant erosion of trust from our customers.
In scenarios like these, having a comprehensive strategy, like a Disaster Recovery Plan (DRP) or a Business Continuity Plan (BCP) component proves invaluable. These plans are instrumental in restoring systems to a functional state.
But what missteps must occur for a criminal to successfully carry out their attack? The answers to this question and more will be explored in this article.
Every attack begins with the reconnaissance phase, which involves gathering information about the target. The reconnaissance phase itself is divided into two methods.
A well-executed reconnaissance allows the attacker to gather a wealth of information about the software/technology used in the company (perhaps from job postings), and it also helps identify many systems accessible from the internet (which may be long-forgotten by companies but pose a real threat).
The amount of information we “leak” to criminals during reconnaissance largely depends on us. We live in a time where practically anyone can find a lot of information about us on social media platforms, which could be useful in subsequent stages of an attack.
In business environments, LinkedIn is an extremely popular social media platform. Attackers can use it to gather information about a company’s employees, technologies, and other critical details.
Let’s assume the attacker’s target is a specific company.
The first thing a cybercriminal might do is visit the company’s profile on the mentioned platform. At this point, they gain information about the employees. In addition, they obtain the company’s website address from the profile, where they can surely find email addresses, such as those for Customer Support.
Furthermore, from the company’s profile, job listings can be explored, revealing details about technologies used by the company, including specific versions—information that is particularly valuable, especially for positions related to IT.
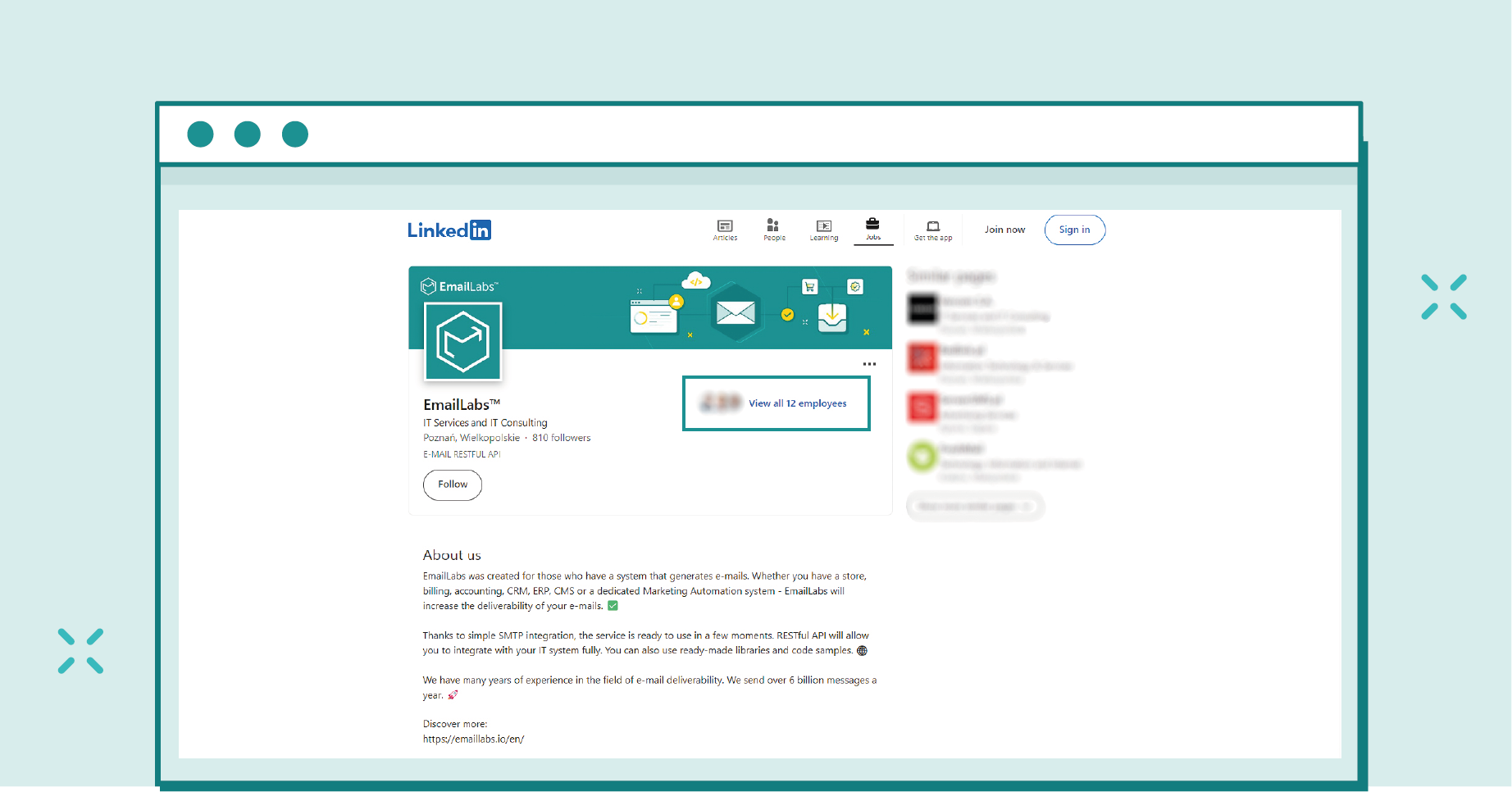
Even if you don’t have an account on LinkedIn or don’t follow a specific company, you can still find out who works at a specific location.
Hackers preparing for an attack will certainly use such information. After reviewing a company’s profile, the attacker may begin to look through the employees’ profiles, where they can find no less information.
It’s worth adding that more information can be extracted by adding someone to your network on LinkedIn (usually, people accept new connections without much thought, just to expand their reach). Having such a person in our social network, we can visit their profile to obtain information from the “Contact Info” tab about:
Sometimes in the “Experience” section, we might find information about the exact duties within the company, for example, what software we work with. This and other information will certainly facilitate the attacker in preparing the attack or selecting specific targets.
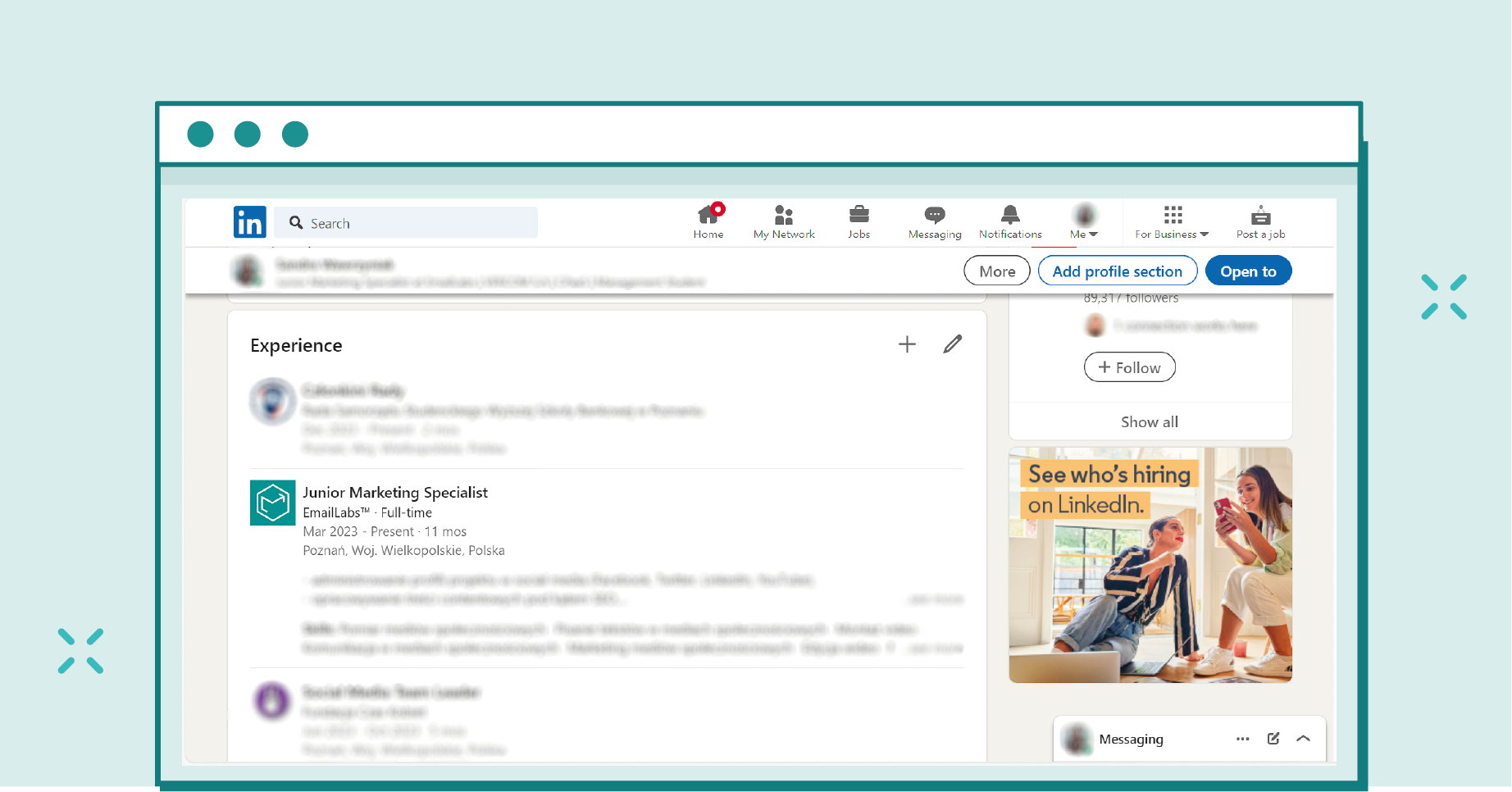
Many users describe their experience with a particular company in more detail, unaware they may be providing information to cybercriminals.
Phishing has become a common occurrence nowadays, and we’ve even discussed it as part of the CyberLabs series.
CyberLabs #1 – Phishing being one of the most popular cyber threats
The fact that phishing is one of the most frequently chosen and effective methods for attackers to gain access to a company’s internal network does not surprise anyone.
Personally, I believe that well-prepared phishing is challenging to detect, especially by less experienced users (for methods related to analyzing and detecting malicious messages, I refer you to the latest CyberLabs article).
Certainly, the primary goal of the message is to prompt us to either click on a specified link to trick us into providing our login credentials (for example, to our email account) or to download and install malicious software. The latter would grant the attacker access to our computer and, consequently, the corporate network.
As we read a few months ago, Twilio reported a phishing attack where employees received SMS messages purportedly from the IT department. The messages claimed that their passwords had expired, and as a result, they needed to log in at a specified URL to change their passwords (of course, the URL was controlled by the attacker).
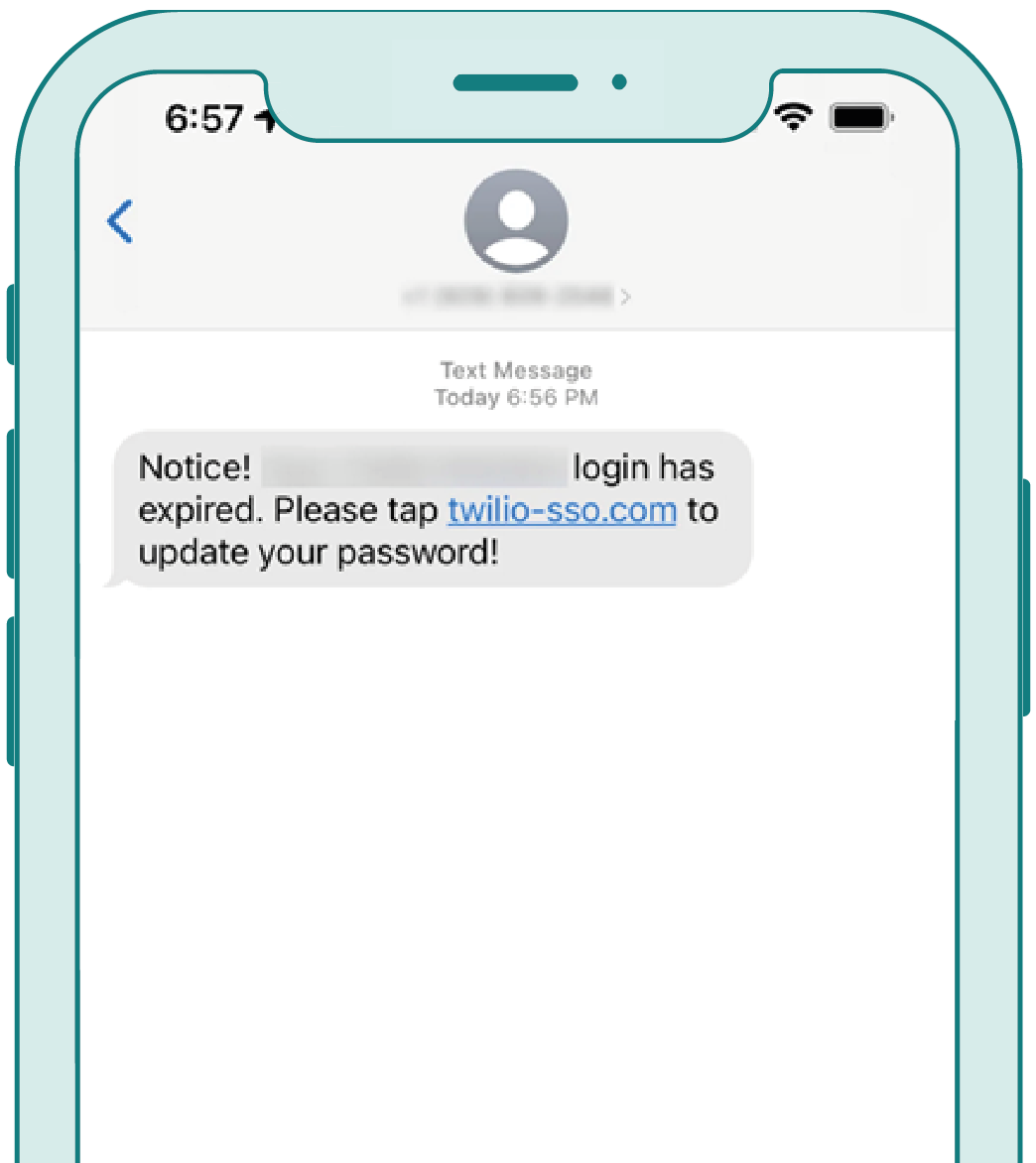
source: https://www.twilio.com/blog/august-2022-social-engineering-attack
Another attack, this time utilizing vishing and spammy push notifications, affected Cisco a few months ago. There are many more similar cases; as you can see, they also affect large companies.
We hear about data breaches as frequently as we do about phishing attacks. Virtually, there is no person in the world whose password hasn’t leaked from some service.
Leaks occur due to various vulnerabilities in web applications, whether through old publicly accessible systems that everyone has long forgotten or through breaches resulting from, for example, the launch of malicious software after infiltrating a particular organization.
Many leaks are publicly available, and practically anyone can access such databases without a problem. If such a database was stolen from a social network or some online store, there is a good chance that a criminal could find many accounts set up with company email addresses.
If such an account uses a simple password, and to make matters worse, the account owner uses the same password across many other corporate systems (perhaps including email accounts) and does not have two-factor authentication (2FA), it doesn’t take much for a criminal to take control of such accounts.
Someone might argue that searching and sifting through massive databases is very time-consuming. I would agree with that, assuming someone is manually searching for and downloading such databases. However, there are specialized search engines that allow checking whether a particular email address or phone number has been part of a data breach.
An example of such a site would be haveibeenpwned.com. Another example might be dehashed.com, which provides information about leaked passwords or their hashes. Additionally, depending on the breach, the website may display information such as IP addresses, physical addresses, and other details that users may have provided on various platforms.
It is worth remembering that by having 2FA and using a simple password (of course, I don’t encourage this; information on password security was covered in CyberLabs #2 ), we are more resistant to attempts to log into our systems using just that password. The 2FA, especially the hardware key, is also a good “tool” to protect against network security attacks.
The third popular method of attack is a drive-by download. In the case of APT (Advanced Persistent Threat) groups that leverage zero-days, this attack can lead to the automatic download and execution of malicious software immediately after clicking a link (although such attacks are not very common).
However, there is a drive-by download technique that requires minimal user interaction. This is referred to as SocGholish, a malicious campaign that exploits vulnerable websites to embed malicious code. This code generates a pop-up message informing the user that they have an outdated browser version and need to update it to view the page.
A .zip file containing the suspicious code inside is downloaded. Of course, after running the software, our computer is infected…
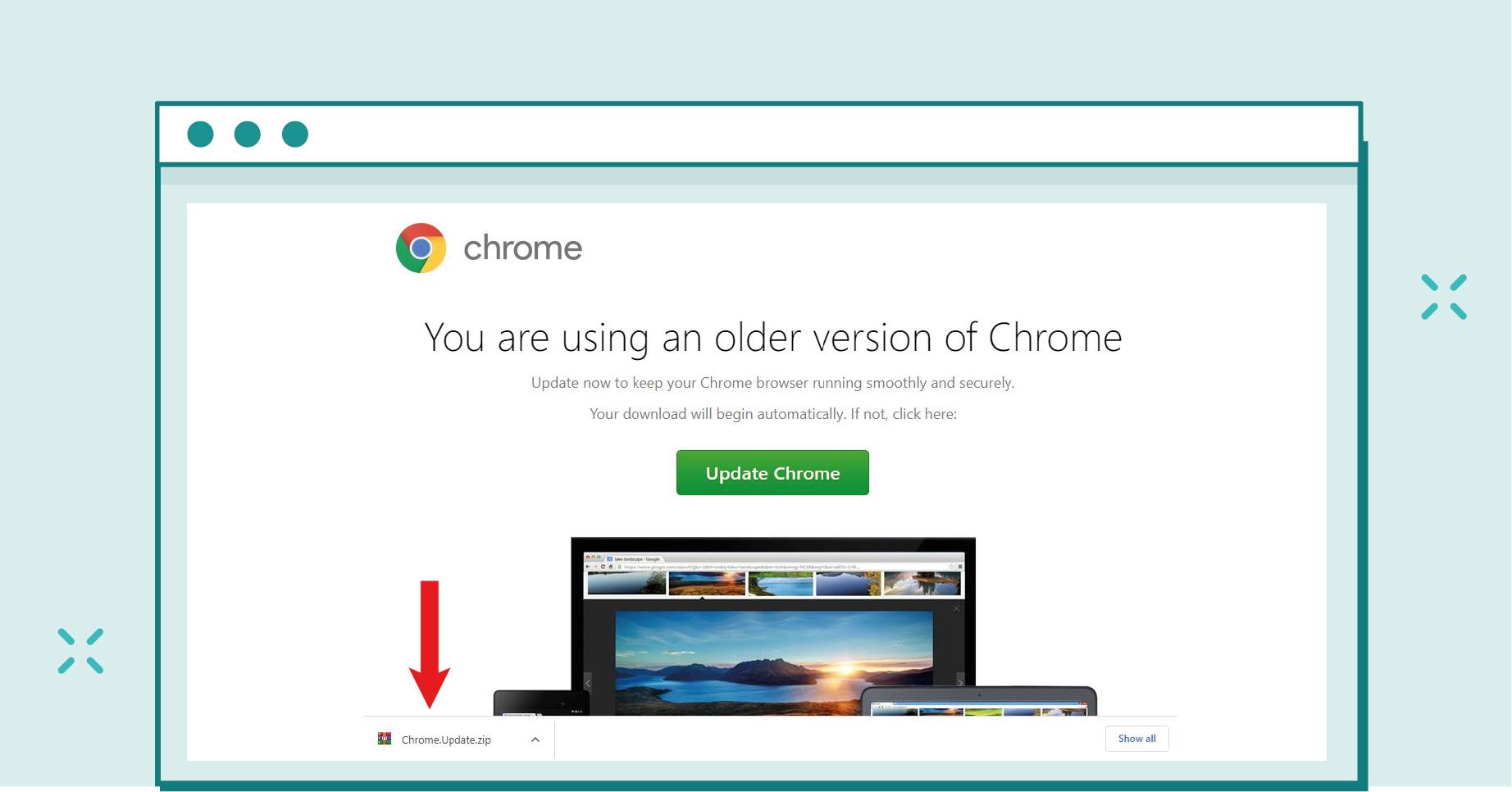
source: https://blog.sucuri.net/wp-content/uploads/2022/11/malicious_browser_update.png
Regardless of how cybercriminals manage to compromise our email accounts, whether through phishing or using leaked passwords, they gain access to many confidential pieces of information. Once inside such an email account, attackers may focus on searching through emails for specific information such as:
Collecting information is not the only thing a criminal can do. Very often, compromised email accounts can be used to send messages with malicious software, aiming to gain access to as many machines as possible. The gathered information can contribute to the compromise of additional systems by the cybercriminal.
The infiltration of an attacker into a company’s network is one of the worst situations that can happen to us. A skilled and experienced hacker using various techniques can quickly access more computers in the corporate network.
Typically, the initial goal is to gain the highest possible privileges within the company’s network, making it easier to infect the entire network with ransomware or other malicious software later.
To execute this plan, attackers may exploit vulnerabilities in the software we use or, through request poisoning, impersonate various genuine network resources. This allows them to intercept credentials when attempting to log in to one of these resources.
Indeed, these are often advanced attacks that may not be easily detected without proper security systems analyzing and monitoring our network. It’s crucial to ensure that our corporate networks have adequate security systems in place.
For some companies, implementing such systems for networks may be associated with purchasing often expensive licenses. It’s worth noting that many systems are open-source, and we can successfully use them in our networks.
Implementing such systems should be a priority because they help to quickly identify many external and internal threats, thereby avoiding penalties, ransom payments, and other potential consequences.
Maximize your email deliverability and security with EmailLabs!
After gaining the highest possible privileges and taking over the attacker’s essential machines comes when the attacker starts exfiltrating or simply stealing data. There are numerous methods for data exfiltration, just as there are many methods a cybercriminal can use for an attack. Below are a few popular methods:
Regardless of the method of data theft, we need proper monitoring to catch such practices in time. So, it is essential to be aware of the threats and know how to prevent and respond to them.
A large number of attacks culminate in the deployment of ransomware, which encrypts all our data that was previously stolen. If we do not pay the ransom, our data may be made public, leading to severe consequences.
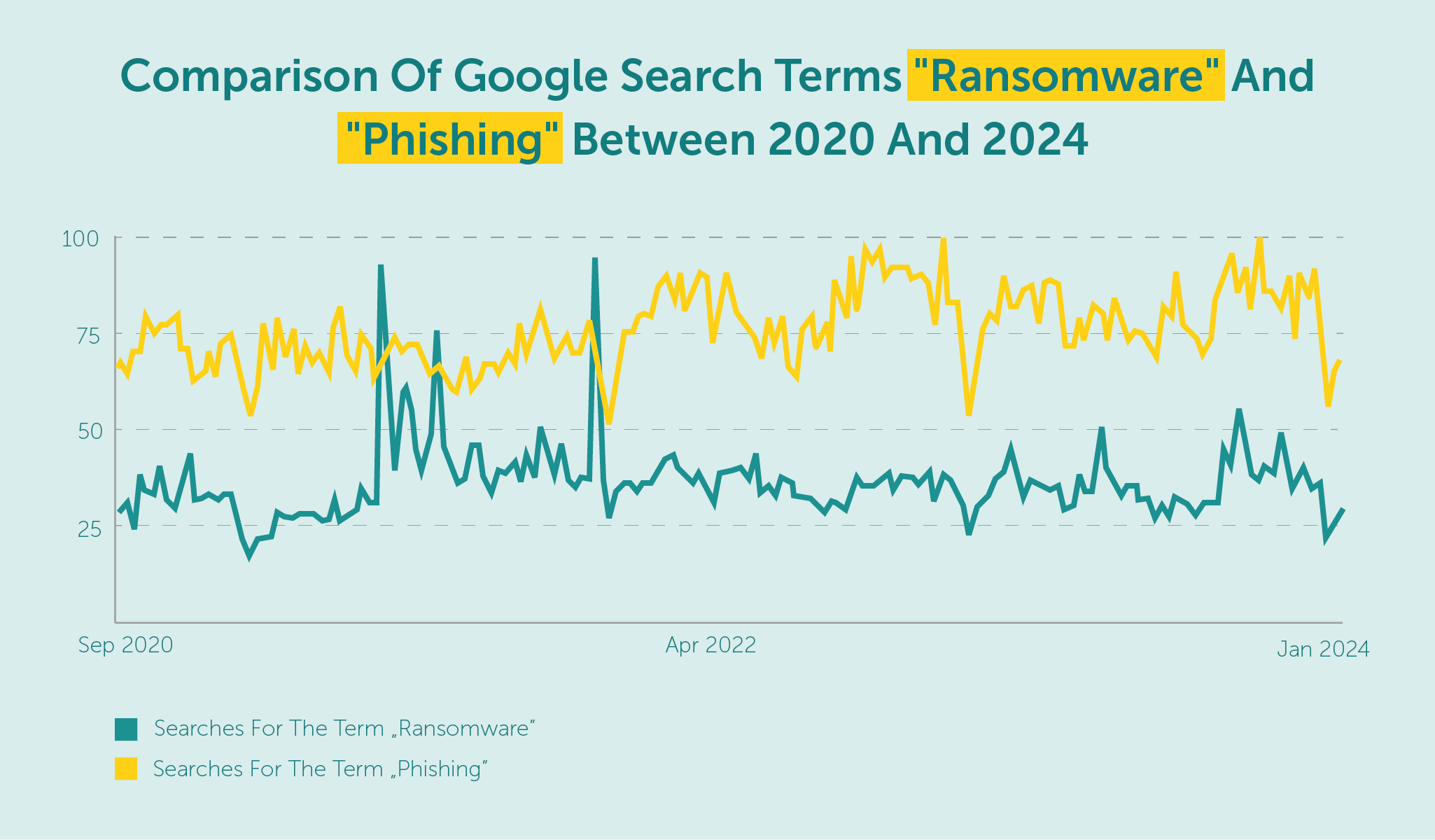
source: Google Trends
However, before this software encrypts all computers and servers, the attackers aim to acquire the highest privileges, as mentioned earlier. Gaining elevated privileges may trigger alarms in security systems; however, despite that, criminals strive to, for example, launch malicious software from the domain controller to encrypt all data.
In recent weeks, there has been an observed increase in ransomware attacks in Poland. This upward trend is also seen globally, so it’s important to keep in mind healthy cybersecurity practices and principles.
Stay Secure!
Most attacks inside a network are hard to catch without proper security systems. So, if you don’t have such systems, it’s worth considering implementing them. Some are open-source, meaning you can use them for free.
We live in a world where your customers switch seamlessly between laptops, smartphones, and tablets. They navigate a complex digital ecosystem – checking emails, using mobile apps, and reacting...
We are delighted to announce that Vercom S.A., the company behind the EmailLabs project, has successfully completed the ISO 22301 certification process. This significant achievement underscores our commitment to...
EmailLabs, as part of the Vercom group, proudly announces its full commitment to aligning its ICT services with the latest cybersecurity standards. In response to dynamically changing regulations, the...
We are pleased to announce that MessageFlow, a product from the Vercom S.A. group, has received the prestigious CSA (Certified Senders Alliance) Certification. This recognition not only underscores the...
Best practices, Maile marketingowe, Marketing E-mails, Transactional Emails
Mass email sending is a critical strategy for business owners, marketers, developers, and nonprofit managers looking to scale their outreach. Whether you are announcing a new product feature, distributing...
Best practices, Marketing E-mails
Customer feedback is the fuel for business growth, but gathering it effectively requires more than just a list of questions. Email surveys remain the most direct channel for understanding...
Best practices, Email Marketing, Pytania i odpowiedzi
Mail merge combines a template document with data to create personalized communications. This technique saves time by automatically generating individualized letters, emails, and labels without manual entry. What Is...
Best practices, Maile marketingowe, Marketing E-mails, Transactional Emails
Mass email sending is a critical strategy for business owners, marketers, developers, and nonprofit managers looking to scale their outreach. Whether you are announcing a new product feature, distributing...
Best practices, Marketing E-mails
Customer feedback is the fuel for business growth, but gathering it effectively requires more than just a list of questions. Email surveys remain the most direct channel for understanding...
Best practices, Email Marketing, Pytania i odpowiedzi
Mail merge combines a template document with data to create personalized communications. This technique saves time by automatically generating individualized letters, emails, and labels without manual entry. What Is...
IT & Tech, Pytania i odpowiedzi, Technical
When an email travels from sender to recipient, it passes through several critical components of email infrastructure. At the heart of this journey sits the Mail Transfer Agent (MTA)...
Best practices, Deliverability, Google and Yahoo's Requirements, Pytania i odpowiedzi
The world of email marketing is constantly evolving, and leading mail service providers – Gmail, Yahoo, Microsoft, and Apple – regularly update their guidelines for senders. In recent years,...
Gmail, Google and Yahoo's Requirements
You might have noticed a new item in your Gmail sidebar recently – the “Manage subscriptions” tab, often flagged with a blue notification dot. While Google announced this feature...
IT & Tech, Pytania i odpowiedzi, Technical
Efficient email communication isn’t just about sending messages — it also involves integrating email functionality into your business systems and applications. Email APIs (Application Programming Interfaces) serve as the...
One of the most important yet often underestimated elements in shaping a company’s brand perception is the transactional email. In e-commerce, the design of such messages must be carefully...
Google and Yahoo's Requirements, Yahoogle
2024 brought fundamental changes to email marketing, introducing new, stringent requirements for senders. Since February 1, 2024, Google and Yahoo have started enforcing new deliverability rules, primarily targeting bulk...