Email Authentication, Security
Email Authentication, Security
DMARC is an email authentication protocol that is designed to give domain owners the ability to protect their domain from unauthorized use, commonly known as email spoofing. Spoofing occurs when a malicious sender sends an email that appears to be from a trusted domain, usually with the intention of phishing, spamming, or distributing malware.
DMARC was created to address this issue by allowing domain owners to specify which mail servers are authorized to send emails on behalf of their domain. By doing so, DMARC enables receivers to determine if an email is legitimate and should be delivered to the inbox or not.
In this article, we will cover everything you need to know about DMARC, including its background, its components, how it works, how to set up a DMARC policy, and common misconceptions about it. To ensure your email domain is secure, take the time to learn more about DMARC and how you can protect yourself from spoofing attacks.
DMARC stands for “Domain-Based Message Authentication, Reporting, and Conformance.” It is a domain alignment reporting mechanism that uses existing email authentication mechanisms, SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail), to give email domain owners the ability to protect their domain from unauthorized use.
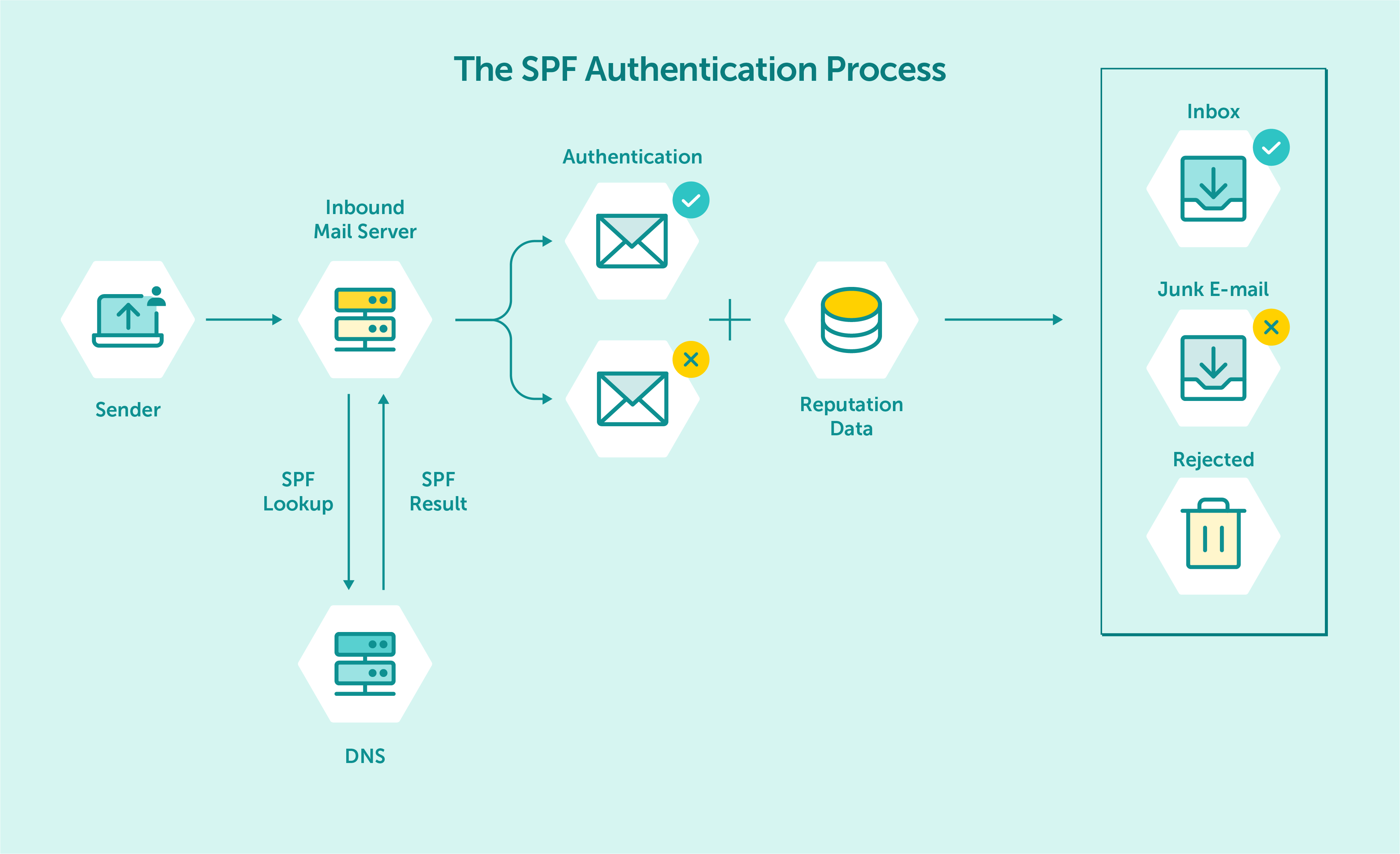
Diagram of how the SPF record works
DMARC policy that a domain owner publishes in their Domain Name System (DNS) record instructs the receiving mail server how to handle emails that fail DMARC authentication. DMARC policies can be set to either “none,” “quarantine,” or “reject.”
A “none” policy instructs the receiving server to take no action, a “quarantine” policy instructs the receiving server to place the email into the recipient’s spam folder or flagged as suspicious, and a “reject” policy instructs the receiving server to reject the email outright.
It should be noted that, unlike SPF and DKIM, DMARC does not serve as an authentication tool in itself.
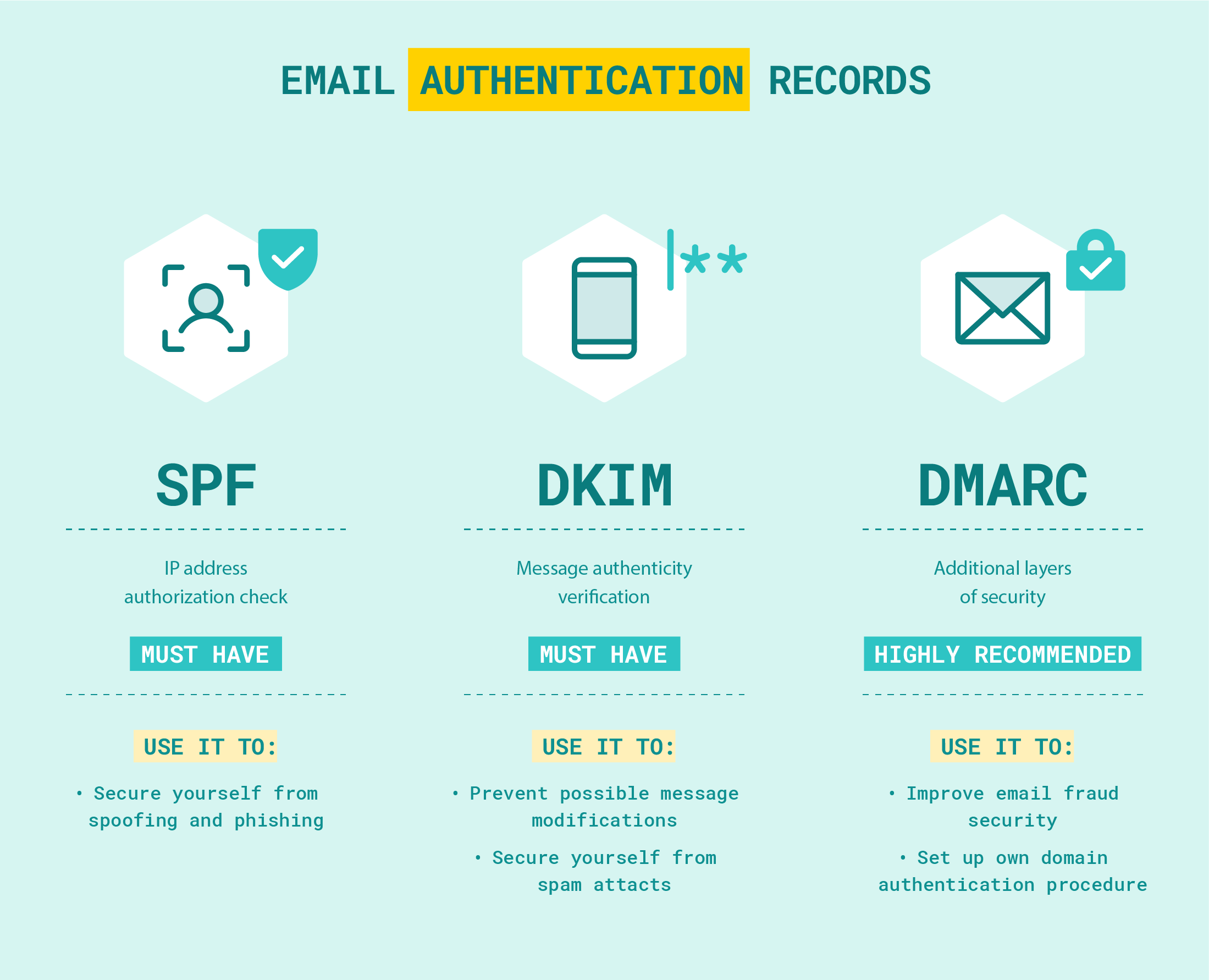
SPF, DKIM, DMARC: Basic elements of email authentication
At the core, DMARC is an important tool for email security. It allows the domain owner to protect their domain from being used for malicious purposes, such as phishing, spamming, and malware distribution. All of these can be executed under the guise of a trusted domain, making it difficult for email users to discern between legitimate and malicious emails.
In simple terms, malicious actors can exploit email authentication mechanisms, such as SPF and DKIM, by spoofing the “From” address of an email and making it appear as though it was sent from a trusted domain. Such an address is virtually indistinguishable for a casual email user, making a way for malicious actors to bypass the email validation system.
Needless to say, this can have serious consequences. Not only can it lead to users unknowingly downloading malicious software or falling victim to phishing attacks, but it can also damage the reputation of the domain being spoofed.
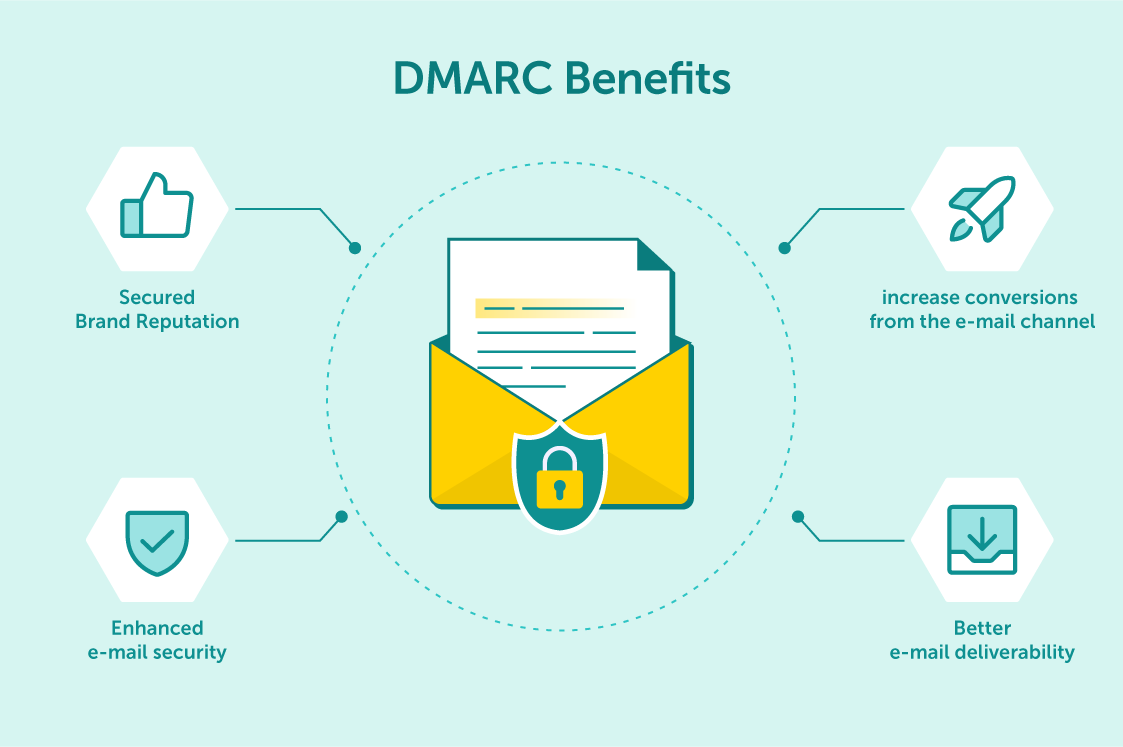
The implementation of DMARC brings many benefits to your company
Domain-Based Message Authentication Reporting and Conformance works by combining two existing email authentication mechanisms, SPF and DKIM, and adding an additional layer of policy. SPF allows the domain owner to specify which mail servers are authorized to send emails on behalf of their domain, while DKIM allows the domain owner to add a digital signature to their emails, verifying that they are authentic and were not forged or changed during transit.
When a receiving mail server receives an email that claims to be from a domain with a published DMARC policy, it will first check the SPF record to ensure that the sending server is authorized to send emails on behalf of that domain. It will then check the DKIM signature to ensure that the email has not been modified between the sending and recipient servers.
If the email passes both authentication checks, the receiving server will deliver the email to the recipient’s inbox. If the email fails either authentication check, the receiving server will check the DMARC policy to determine how to handle the email. Depending on the DMARC policy, the email message may be delivered, placed in the spam folder, or rejected outright.
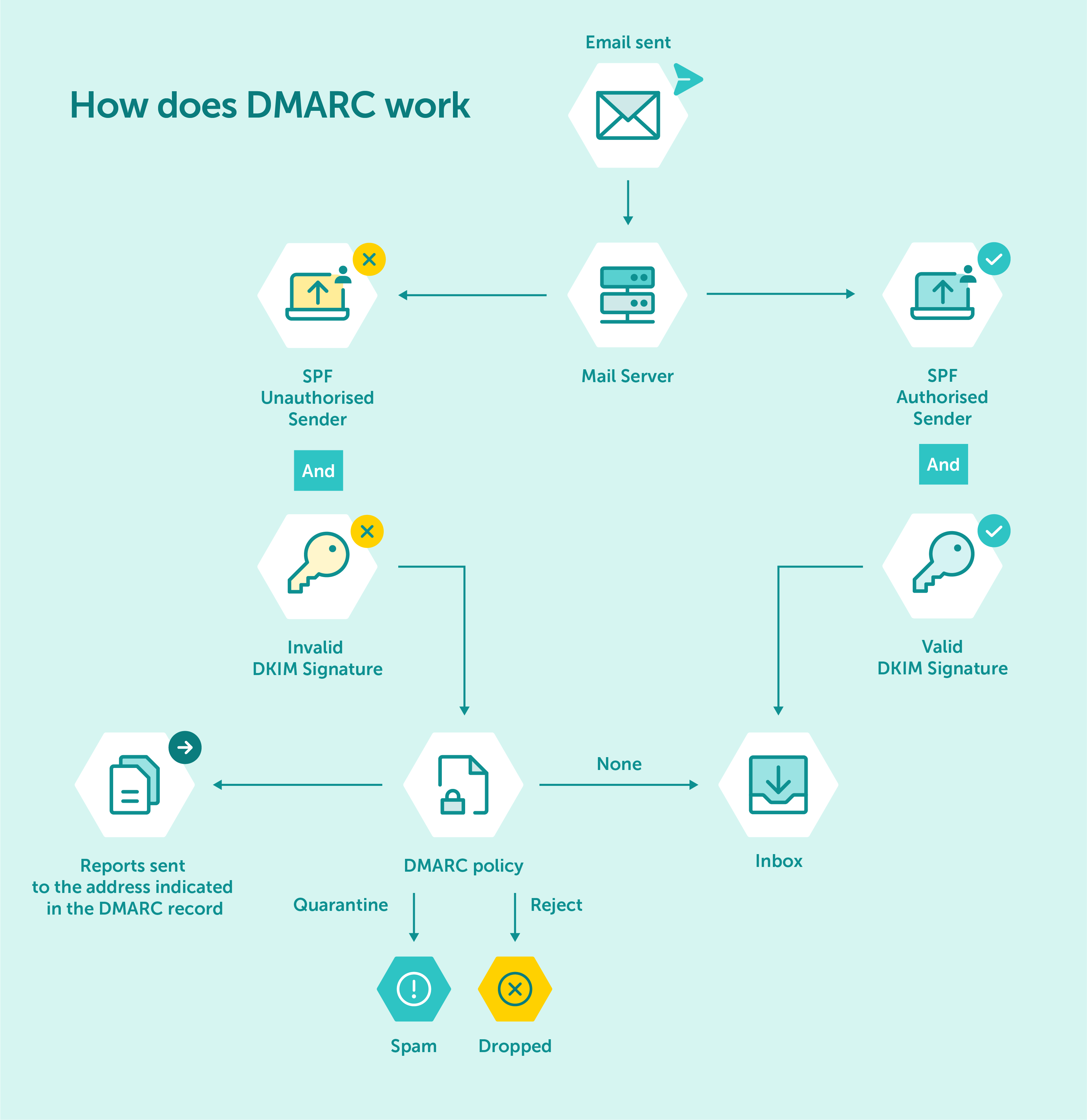
Diagram of how the DMARC protocol works
DMARC record alignment refers to the comparison between the domain name in the From address and the domains associated with SPF and DKIM authentication checks. SPF authenticates the domain that appears in the Return-path (MAIL FROM), while DKIM authenticates the domain found in d= tag inside the DKIM signature. DMARC requires at least one of the domains above to match the From header. There are two types of DMARC record alignment modes: relaxed and strict.
In relaxed mode, two domains don’t have to match exactly, in strict mode on the other hand, two domains must be identical to be in alignment.
The alignment mode for DKIM signature is indicated by the adkim tag, while aspf tag refers to the alignment mode for the SPF.
Maximize your email deliverability and security with EmailLabs!
Setting up a DMARC policy is fairly straightforward. All you need to do is add a DMARC record to your DNS.
To do this, you will need to access DNS settings in the Admin Console and add a TXT record that looks something like this:
v=DMARC1; p=quarantine; rua="[email protected]"; ruf="mailto:[email protected]"
In this record, the “v” tag indicates the DMARC version being used (“DMARC1” by default), the “p” tag indicates the DMARC policy, and the “rua” and “ruf” tags indicate which email addresses should receive reports regarding DMARC-related activity – “rua” for aggregate reports and “ruf” for failure/forensic reports. If you use the rua/ruf tag, you must use the “mailto:” prefix.
Optional tags:
Once you save the record, you will need to wait up to 72 hours for the new DNS records to propagate. Once this is done, your DMARC policy should be in effect, and you can start monitoring its effects on incoming emails.
Once you have a DMARC policy in place, it’s important to analyze the reports that are generated by receiving servers. These reports contain information about any emails that fail authentication checks as well as details on how they were handled according to the DMARC policy.
An aggregate report contains statistical data about all of the emails sent from your domain over a specific time period. This data includes the total number of emails sent, how many passed authentication checks, and how many failed.
A forensic report contains detailed information about a single email message that fails authentication checks. This data can be used to determine why an email failed authentication and take steps to prevent similar failures in the future. Due to concerns regarding privacy and compliance, many organizations opt not to request ruf reports as they often contain sensitive data.
Both types of reports are important for understanding your DMARC policy’s performance and making necessary adjustments to ensure the highest email security possible.
Once you have a DMARC policy in place, it’s important to remember that it is not set in stone. As your organization’s email usage changes or new threats emerge, it may be necessary to update your DMARC policy. For instance, you may want to change your policy to quarantine or reject emails if the number of malicious emails sent from “your” domain increases.
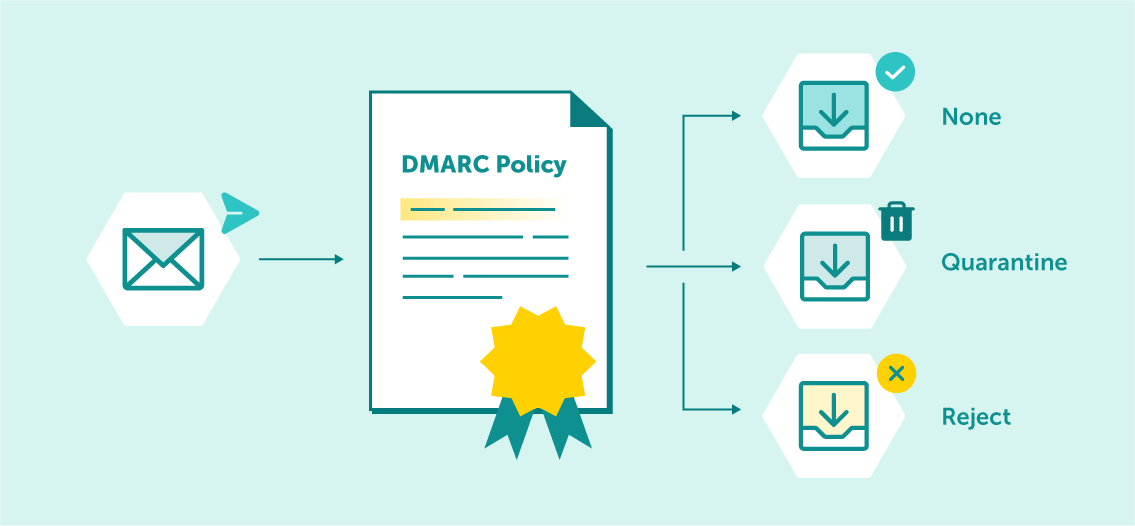
DMARC policy states how to treat emails sent from a particular domain
The key is to stay vigilant and monitor your DMARC reports for any signs of malicious activity. If you do detect an increase in suspicious emails, it may be time to update your policy or take additional steps, such as implementing stricter authentication measures.
Although DMARC is an important email security tool, there are some common misconceptions about it. The most prevalent of these stem from the wrong assumption that DMARC is an active security measure. This is not the case – DMARC does not actively block malicious emails, it only instructs the receiving server how to handle them once they have failed authentication checks. Here are a few other common misconceptions to be aware of:
Another common misconception about DMARC is that it only protects against spoofing attacks. While DMARC is an effective tool for detecting and blocking spoofed emails, it also provides valuable insights into legitimate email traffic. By analyzing DMARC reports, organizations can gain visibility into which email servers are sending messages on their behalf and identify any unauthorized senders.
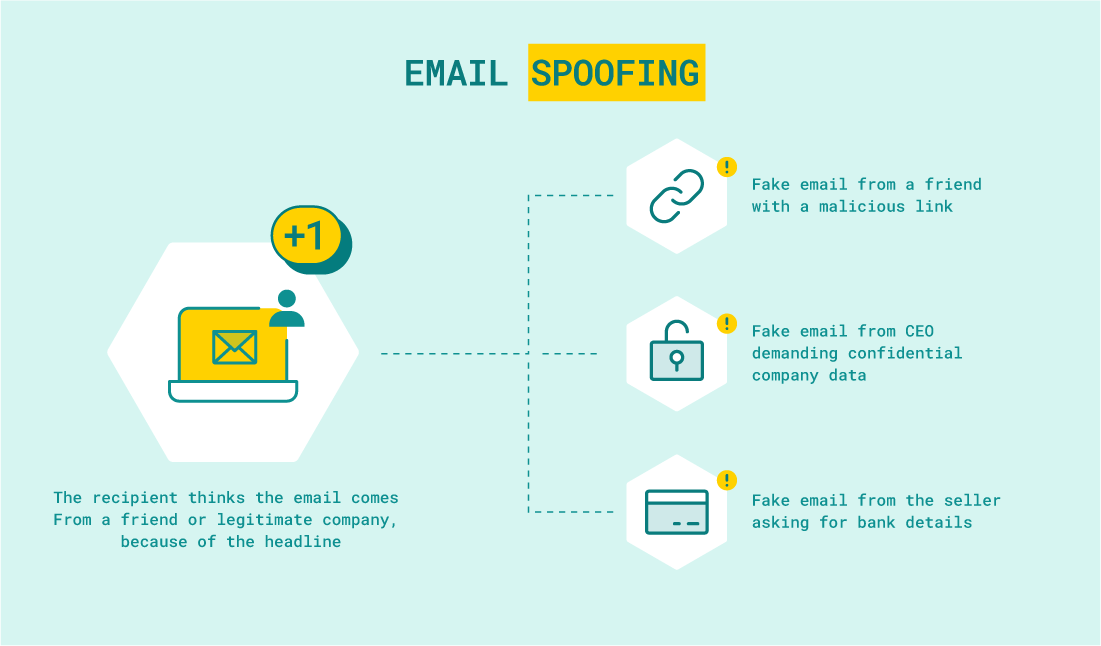
During some attacks, cybercriminals study the target of their attack very carefully to lull the recipients’ alertness. They use appropriate language and add characteristic data/phrases.
Additionally, DMARC provides a mechanism for email receivers to provide feedback to email senders about the disposition of their messages. This feedback loop can help organizations identify and correct issues with their email authentication infrastructure and improve the deliverability of their legitimate messages.
Maximize your email deliverability and security with EmailLabs!
One of the most persistent DMARC myths is that the protocol will inevitably break legitimate emails. This misconception arises from a misunderstanding of how DMARC policies work. DMARC policies specify how receivers should handle messages that fail authentication checks. By default, DMARC policies are set to “none,” which means that receiving servers will not take any action if a message fails DMARC checks.
To avoid breaking legitimate emails, it is essential to gradually increase DMARC policy strictness over time. This approach allows organizations to identify and address any issues with their email authentication infrastructure before fully enforcing DMARC policies. By starting with a “none” policy, companies can gradually move to a “quarantine” policy (where suspicious messages are typically delivered to the recipient’s spam folder) and eventually to a “reject” policy (where suspicious messages are rejected outright).
Some organizations may believe that DMARC is only necessary for large enterprises with complex email infrastructures. In reality, however, DMARC is essential for any organization that uses its own email infrastructure and wants to protect its brand, customers, and partners from phishing and spoofing attacks.
While larger organizations may have more complex email systems to manage, small and mid-sized organizations are just as vulnerable to email-based attacks. In fact, smaller organizations may be even more vulnerable since they may lack the resources to implement robust email security controls – and implementing DMARC reports can help with that.
Finally, some people may mistakenly believe that DMARC works like a spam folder. While it is true that DMARC policies can be set to “quarantine” suspicious messages, this does not mean that all of those messages will automatically get sent to the recipient’s spam.
Instead, quarantined messages will be further analyzed by the receiving email server before being delivered. If a message passes additional checks, it will be delivered to the recipient’s inbox – even if it originally failed preliminary DMARC authentication checks. There, data from both aggregate and forensic reports can help identify malicious emails and take preventive measures accordingly.
DMARC is an important email authentication protocol that allows domain owners to protect their domains from unauthorized use. It combines existing email authentication mechanisms, such as SPF and DKIM, with a policy-based approach to determine how emails that fail SPF authentication checks and DKIM signature validation should be handled by the receiving mail server.
By setting up a DMARC policy and monitoring its performance over time, organizations can gain valuable visibility into which servers are sending messages on their behalf and take steps to mitigate any potential threats. Additionally, implementing DMARC policies for smaller organizations is just as important – if not more so – in order to ensure proper brand protection and customer safety. If you have any more questions, don’t hesitate to contact us – we’ll be happy to help you find the solution that is perfect for your company.
Gmail has announced significant changes in the requirements for email senders to maintain a good reputation and proper classification of messages in user inboxes starting from February 1, 2024....
Vercom S.A. public joint-stock company to which the EmailLabs project belongs, has been assessed and certified to be compliant with the ISO/IEC 27001 and ISO/IEC 27018 standards. The Vercoms’...
The increasing number of phishing attacks each year, and the projection that this trend will continue to escalate, aren’t likely to astonish anyone. This can be attributed, in part,...
Out of all the things that can go wrong when sending out marketing emails, having your emails end up in the recipient’s spam folder is arguably the most dreaded...
Email Authentication, Security
DMARC is an email authentication protocol that is designed to give domain owners the ability to protect their domain from unauthorized use, commonly known as email spoofing. Spoofing occurs...
With the emergence of the Covid-19 pandemic, many brands have been challenged to adapt in a short period to the changed reality and new consumer attitudes. That meant reorganizing...
Have you ever sent an email in haste and immediately wished you hadn’t? It happens more often than we’d like to admit. If you ever find yourself in this...
One safe and easy way to keep track of your digital interactions is to save emails as PDFs. However, do you know the best ways to easily turn your emails into PDF files? In this article, we’ll look into the different ways you can do to turn your emails into accessible PDF files. Let’s start! Key Takeaways To save emails...
Sending large files online can sometimes feel like maneuvering through a maze with unexpected twists and turns. The frustration of hitting attachment size limits or dealing with slow uploads...
Have you ever sent an email in haste and immediately wished you hadn’t? It happens more often than we’d like to admit. If you ever find yourself in this...
One safe and easy way to keep track of your digital interactions is to save emails as PDFs. However, do you know the best ways to easily turn your emails into PDF files? In this article, we’ll look into the different ways you can do to turn your emails into accessible PDF files. Let’s start! Key Takeaways To save emails...
Sending large files online can sometimes feel like maneuvering through a maze with unexpected twists and turns. The frustration of hitting attachment size limits or dealing with slow uploads...
Are you a bit baffled by email protocols like IMAP, POP3, and SMTP? Have no fear – this article is here to explain it all. If you have ever...
In 2024, global providers like Gmail and Yahoo have implemented a series of changes, primarily targeting bulk senders. These changes, already in effect, are part of a continuous update...
In the face of dynamic technological advancements and increasingly sophisticated cyber threats, ensuring network security has become crucial. Dozen security incidents present a challenge that we cannot afford to...
Google and Yahoo's Requirements
2024 marks a turning point in the fast-paced world of email deliverability, as this is the year when Google and Yahoo updated their sender requirements. With the enforcement period...
Best practices, Email Marketing
B2B email marketing – it’s a term you’ve likely heard before, but what does it really entail? And, more importantly, how can it be done effectively? In this article,...
Deliverability, Sending Reputation
Email sender reputation is one of the most important factors that can determine whether your emails reach the intended recipient or not. So, what is the email sender reputation,...