Spam Traps are email addresses used by ISPs, various spam-fighting organizations, and Blacklist administrators to identify and monitor the mailings of senders who do not follow good mailing practices when it comes to verifying their contact databases. The aim of their use is to reduce the amount of spam that reaches our mailboxes every day.
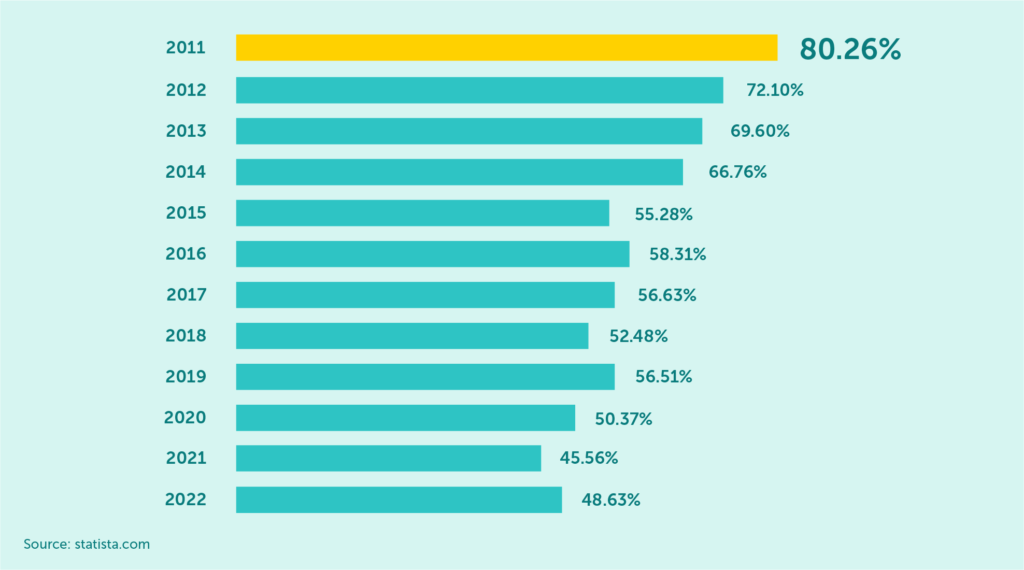
Global spam volume as percentage of total e-mail traffic from 2011 to 2022
There are many types of Spam Traps. Most of the time, Spam Traps are email addresses that have been inactive for a long. They can also be recycled email addresses that were once active but are no longer in use, or they can be newly created addresses that have never been used before. In all cases, however, a Spam Trap set up with the intention of catching senders who do not properly verify their contact lists.
If your mailing list contains these types of email addresses, it may mean you are not taking proper care of its hygiene. This can result in your messages being flagged as spam and your IP address being blacklisted. In the worst case, it can even lead to your email service provider shutting down your account.
Using EmailLabs, you can avoid falling into such a trap, as our system has a built-in Spam Trap address filter. When you send a message to an address on our internal, regularly updated list, the sending will be automatically blocked, and the message will receive a “dropped” status. It is important to note that our tool is not designed to clean old contact databases or to find Spam Trap addresses, so such addresses will not be marked in any additional way. To maintain the high deliverability of emails, always send them only to verified and up-to-date recipients.
That’s why it’s important to be aware of what spam traps are and how to avoid them.
Read on to learn more.
Maximize your email deliverability and security with EmailLabs!
When talking about Spam Traps, it is impossible not to mention a particular type of trap – the Honeypot. In cyber security, this term refers to a strategy that relies on the use of appropriately crafted methods (in this case, email addresses) to detect unauthorized processing and reveal the perpetrator.
Such Spam Traps are particularly troublesome for spammers because ISPs or anti-spam organizations do not wait until an address is in the subscriber’s database and someone accidentally sends an email to it.
These addresses are deliberately promoted and made public directly on websites or embedded in their code. Web scraping bots are able to find such addresses and collect them into their database.
Once emails start reaching the mailbox, the active spammer can be located, blocked, and reported to the relevant organization fighting spam.
This Spam Trap can therefore be compared to a pot of honey exposed to the sun – all you have to do is wait patiently, and the insects will be tempted to fly to it themselves.
We usually only become aware that Spam Traps may be present on our mailing list when the delivery rate starts to drop, and we have checked out other potential causes of this phenomenon.
Identifying specific Spam Trap email addresses is not easy – such information is not publicly available, as it would counter the purpose of their existence – spammers would easily exclude them. However, there are several ways to find potential Spam Traps – the key is to track engagement.
A recipient who doesn’t open your emails for several months, doesn’t complete orders, doesn’t use the password reminder, and doesn’t get in touch with you themselves (technical requests/complaints, etc.) could be a Spam Trap (or soon become one).
To be sure, you can segment your contact group and implement a reactivating campaign only for unengaged recipients. If your emails still do not get opened, remove such addresses from your mailing list. Even if they are not Spam Traps, the lack of any response can mean one thing – the recipients are not interested in receiving any correspondence from you.
There are also a number of paid tools available on the Internet that allow you to check for Spam Traps in your mailing list – some of the more popular ones are, for example, ZeroBounce or Email List Verify. You can upload your contact database to these platforms, and they will analyze it for you.
ZeroBounce – email address verification tool
“Spam Traps are an issue that every email marketer needs to be aware of. They can be detrimental to your sending reputation and completely damage the performance of your campaign,”
– says Brian Minick, COO of email validation platform ZeroBounce.“It’s important you are always checking to see if spam traps live on your list. While in theory a good sender would not have them, we’ve seen examples of even the best senders having them added to their newsletter sign-ups maliciously. You never know if they are lurking on your list as, in many cases, they appear to be just a normal looking email address. They’re also being created every day and new ones can appear. It’s critical you get these off and never send to them.
A good validation service such as ZeroBounce can ensure we help get them off your list.”
Fortunately, there are several ways to avoid Spam Traps. The most important thing is to verify the quality of your contact database on an ongoing basis. Some of the foolproof methods you can use to achieve this include the following:
By following these simple rules, you will protect your emailing campaigns against the risk of being trapped by a Spam Trap.
Maximize your email deliverability and security with EmailLabs!
What consequences you face when sending messages to spam trap addresses depends on the type of trap you get ‘caught in.’ If you make a single mailing to invalid addresses with a typo, there should be no reputational impact as long as it involves, for example, registering and sending a double opt-in message (to confirm enrolment), which will shut down further attempts to communicate with the same recipient.
However, multiple mailings to spam trap email addresses (especially a pristine spam trap) can have significant negative consequences – such as a weakening sender reputation, being blacklisted by RBLs, and a decrease in deliverability rates.
The fight against spam is constant. Every day, our inboxes are flooded with emails we do not want.
So let’s remember that Spam Traps are not intended to make it difficult for legitimate senders to carry out their mailings – those who take proper care of the hygiene of their mailing list and send out campaigns only to contacts interested in receiving emails from them, have nothing to fear.
Spam Trap email addresses are allies in the fight against spammers who block visibility in the mailbox for your messages – looking at them this way, you may find them a useful tool.
We are proud to announce that Vercom S.A., the company behind the EmailLabs project, successfully passed an audit for compliance with the latest ISO/IEC 27001:2022 and ISO/IEC 27018:2019 standards....
Gmail has announced significant changes in the requirements for email senders to maintain a good reputation and proper classification of messages in user inboxes starting from February 1, 2024....
The increasing number of phishing attacks each year, and the projection that this trend will continue to escalate, aren’t likely to astonish anyone. This can be attributed, in part,...
Out of all the things that can go wrong when sending out marketing emails, having your emails end up in the recipient’s spam folder is arguably the most dreaded...
Email Authentication, Security
DMARC is an email authentication protocol that is designed to give domain owners the ability to protect their domain from unauthorized use, commonly known as email spoofing. Spoofing occurs...
With the emergence of the Covid-19 pandemic, many brands have been challenged to adapt in a short period to the changed reality and new consumer attitudes. That meant reorganizing...
Are you frustrated with the constant struggle of your emails getting blocked by Gmail? Have you ever wondered about the reasons behind this issue and, more importantly, how to...
In the ever-evolving landscape of email management, Google has announced an exciting upgrade to Gmail’s summary cards, aimed at improving user experience and streamlining inbox navigation. The latest enhancements,...
Antispam, Best practices, Dobre praktyki
Entering the world of email communication, you’ll encounter many terms that initially seem straightforward and intuitive. However, some of these can be pretty challenging. Accurately distinguishing between them is...
Are you frustrated with the constant struggle of your emails getting blocked by Gmail? Have you ever wondered about the reasons behind this issue and, more importantly, how to...
In the ever-evolving landscape of email management, Google has announced an exciting upgrade to Gmail’s summary cards, aimed at improving user experience and streamlining inbox navigation. The latest enhancements,...
Antispam, Best practices, Dobre praktyki
Entering the world of email communication, you’ll encounter many terms that initially seem straightforward and intuitive. However, some of these can be pretty challenging. Accurately distinguishing between them is...
Attaching a folder to an email may seem complicated at first glance, especially if you’re trying to send multiple files or an entire project’s documents to a colleague or...
Best practices, Deliverability
In today’s digital age, email has become an integral part of our personal and professional communication. We rely heavily on emails to send important messages, documents, and updates. But...
We are proud to announce that Vercom S.A., the company behind the EmailLabs project, successfully passed an audit for compliance with the latest ISO/IEC 27001:2022 and ISO/IEC 27018:2019 standards....
Best practices, Deliverability
Are you struggling to improve the deliverability and engagement of your email marketing campaigns? Look no further than email subdomains. You can protect your root domain and effectively manage...
What is the darknet? Shrouded in mystery for many years and often associated with ominous connotations, the darknet is a part of the internet that evokes curiosity, fascination, and...
A few weeks ago, at Vercom, we began the process of implementing the NIS2 Directive and preparing to meet the requirements of the Digital Operational Resilience Act (DORA). What...